Cybersecurity News
US troops deploying to the Middle East told to leave personal devices at home
US military officials fear operational security (OpSec) failures in handling personal devices might put soldiers in danger.Don't Lose That Device
Did you know you are 100 times more likely to lose a laptop or mobile devices than have it stolen? When you are traveling, always double-check to make sure you have your devices with you, such as when leaving airport security, exiting your taxi or check out of your hotel.The five: ransomware attacks
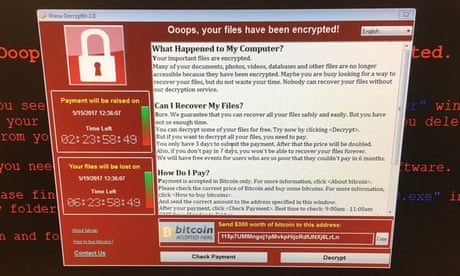 Software that demands money with menaces has hit the big time. Here are some of its most lucrative forms
Software that demands money with menaces has hit the big time. Here are some of its most lucrative formsCyber-attacks that threaten to publish a victim’s data or block access to it unless a ransom is paid have grown internationally since 2012.
Continue reading...Academic research finds five US telcos vulnerable to SIM swapping attacks
Researchers find that 17 of 140 major online services are vulnerable to SIM swapping attacks.Proof-of-concept code published for Citrix bug as attacks intensify
Two Citrix bug (CVE-2019-19781) exploits have been published on GitHub yesterday, making future attacks trivial for most hackers.Alleged Member of Neo-Nazi Swatting Group Charged
Federal investigators on Friday arrested a Virginia man accused of being part of a neo-Nazi group that targeted hundreds of people in "swatting" attacks, wherein fake bomb threats, hostage situations and other violent scenarios were phoned in to police as part of a scheme to trick them into visiting potentially deadly force on a target's address.Synopsys Buys Tinfoil
Tinfoil Security's dynamic application and API security testing capabilities will be added to Synopsys Software Integrity Group.Major Brazilian Bank Tests Homomorphic Encryption on Financial Data
The approach allowed researchers to use machine learning on encrypted data without first decrypting it.Hundreds of millions of cable modems are vulnerable to new Cable Haunt vulnerability
Cable modems using Broadcom chips are vulnerable to a new vulnerability named Cable Haunt, researchers say.6 Unique InfoSec Metrics CISOs Should Track in 2020
 You might not find these measurements on a standard cybersecurity department checklist. But they can help evaluate risks you haven't even considered yet.
You might not find these measurements on a standard cybersecurity department checklist. But they can help evaluate risks you haven't even considered yet.
Cisco Webex Bug Allows Remote Code Execution
 Cisco patched two high-severity flaws this week, in its Webex and IOS XE Software products.
Cisco patched two high-severity flaws this week, in its Webex and IOS XE Software products.
Lifeline Assistance Phone Users Targeted with ‘Uninstallable’ Adware
 A Virgin Mobile-branded phone distributed by Assurance Wireless to low-income U.S. citizens has a trojan pre-installed that can download additional malware.
A Virgin Mobile-branded phone distributed by Assurance Wireless to low-income U.S. citizens has a trojan pre-installed that can download additional malware.
Indian National Pleads Guilty to Multimillion-Dollar Call Center Scam
The India-based call centers scammed US victims out of millions of dollars between 2013 and 2016.Week in security with Tony Anscombe
Some takeaways from CES 2020 – Firefox update plugs a zero-day – Facebook cracks down on deepfakes
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
Week in security with Tony Anscombe
Some takeaways from CES 2020 – Firefox update plugs a zero-day – Facebook cracks down on deepfakes
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
5 Tips on How to Build a Strong Security Metrics Framework
The carpentry maxim "measure twice, cut once" underscores the importance of timely, accurate, and regular metrics to inform security leaders' risk decisions.Study Points to Lax Focus on Cybersecurity
Despite ranking at the top of respondents' concerns, organizations still show gaps in acting on cybersecurity, Society for Information Management (SIM) report finds.Connected cars: How to improve their connection to cybersecurity
As software becomes more important than ever, how can engaging the security industry make the road ahead less winding?
The post Connected cars: How to improve their connection to cybersecurity appeared first on WeLiveSecurity
Connected cars: How to improve their connection to cybersecurity
As software becomes more important than ever, how can engaging the security industry make the road ahead less winding?
The post Connected cars: How to improve their connection to cybersecurity appeared first on WeLiveSecurity
