Cybersecurity News
Sophisticated P2P Botnet Targeting SSH Servers
'FritzFrog' is fileless, uses its own proprietary P2P implementation, and has breached at least 500 servers so far, Guardicore says.19 August 2020
CISA Warns of New RAT Aimed at US Defense Contractors
Hidden Cobra, an APT group associated with the government of North Korea, is thought to be behind the campaign.19 August 2020
Newly Patched Alexa Flaws a Red Flag for Home Workers
Alexa could serve as an entry point to home and corporate networks. Security experts point to the need for manufacturers to work closely with enterprise security teams to spot and shut down IoT device flaws.19 August 2020
ICS Vulnerability Reports Rapidly Rise
More scrutiny of products for industrial control systems is expected to expose even more weaknesses in devices that run critical infrastructure.19 August 2020
How to Control Security Costs During a Down Economy
Three key areas security professionals should watch when managing their budgets.19 August 2020
Tens of suspects arrested for cashing-out Santander ATMs using software glitch
Santander says it fixed the ATM software glitch that was exploited this week across the tri-state area.19 August 2020
Stolen Data: The Gift That Keeps on Giving
 Users regularly reuse logins and passwords, and data thieves are leveraging that reality to breach multiple accounts.
Users regularly reuse logins and passwords, and data thieves are leveraging that reality to breach multiple accounts.
19 August 2020
Voice Phishers Targeting Corporate VPNs
The COVID-19 epidemic has brought a wave of email phishing attacks that try to trick work-at-home employees into giving away credentials needed to remotely access their employers' networks. But one increasingly brazen group of crooks is taking your standard phishing attack to the next level, marketing a voice phishing service that uses a combination of one-on-one phone calls and custom phishing sites to steal VPN credentials from employees.19 August 2020
WannaRen ransomware author contacts security firm to share decryption key
A major ransomware outbreak hit China back in April.19 August 2020
Airline DMARC Policies Lag, Opening Flyers to Email Fraud
 Up to 61 percent out of the IATA (International Air Transport Association) airline members do not have a published DMARC record.
Up to 61 percent out of the IATA (International Air Transport Association) airline members do not have a published DMARC record.
19 August 2020
The Sounds a Key Make Can Produce 3D-Printed Replica
 Researchers reveal technology called SpiKey that can ‘listen’ to the clicks a key makes in a lock and create a duplicate from the sounds.
Researchers reveal technology called SpiKey that can ‘listen’ to the clicks a key makes in a lock and create a duplicate from the sounds.
19 August 2020
Facebook sued over fact-check messages on anti-vaccination posts
The CHD claims Facebook is “censoring truthful public health posts.”19 August 2020
New FritzFrog P2P botnet has breached at least 500 enterprise, government servers
The botnet kills off competing processes on Linux systems before mining cryptocurrency.19 August 2020
How to prepare and protect your digital legacy
It's never too soon to plan for what will happen to your digital presence after you pass away
The post How to prepare and protect your digital legacy appeared first on WeLiveSecurity
19 August 2020
Some email clients are vulnerable to attacks via 'mailto' links
GNOME Evolution, KDE KMail, IBM/HCL Notes, and older versions of Thunderbird found to be vulnerable.18 August 2020
Ransomware Attack on Carnival May Have Been Its Second Compromise This Year
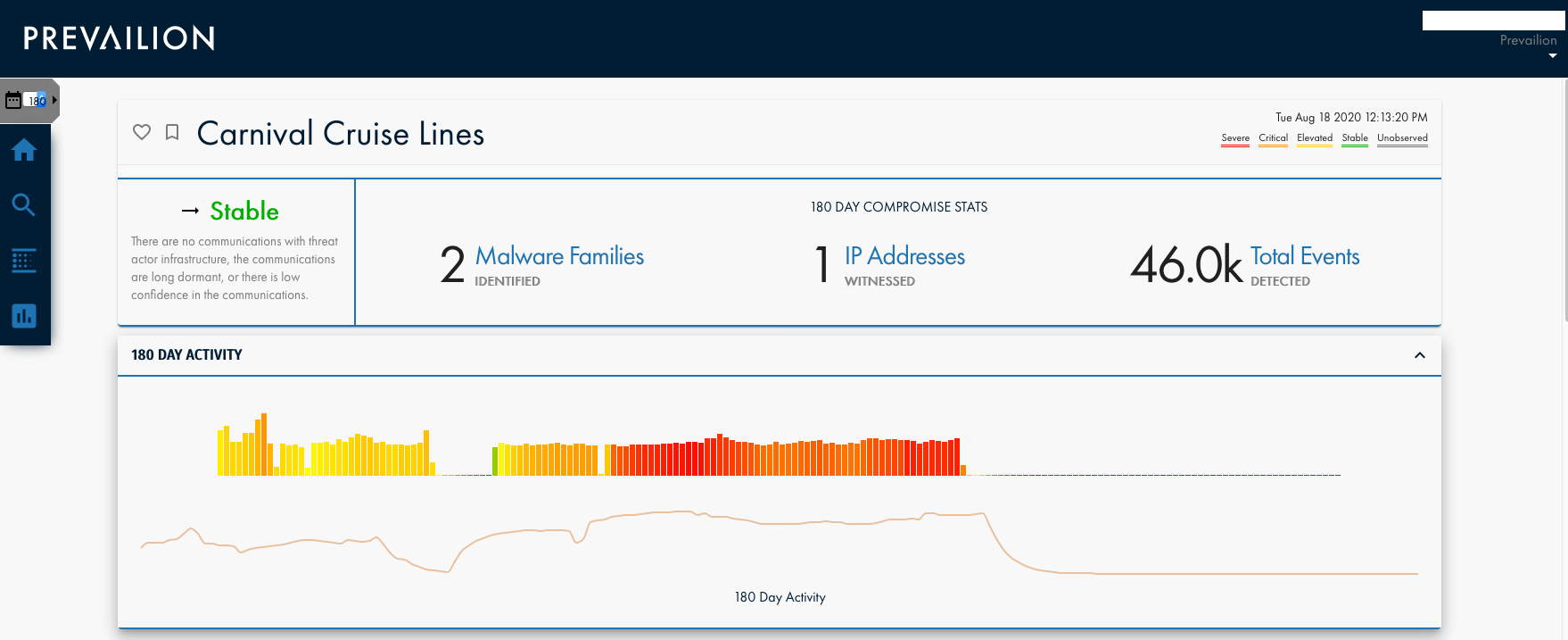 Security vendor Prevailion says it observed signs of malicious activity on the cruise operator's network between at least February and June.
Security vendor Prevailion says it observed signs of malicious activity on the cruise operator's network between at least February and June.
18 August 2020
Canadian Government Issues Statement on Credential-Stuffing Attacks
The government is responding to threats targeting the GCKey service and CRA accounts, which are used to access federal services.18 August 2020
New Campaign Combines Extortion, DDoS
Latest attacks bank on the reputation of two prominent APT groups to increase the threat credibility.18 August 2020
Researchers Warn of Active Malware Campaign Using HTML Smuggling
 A recently uncovered, active campaign called "Duri" makes use of HTML smuggling to deliver malware.
A recently uncovered, active campaign called "Duri" makes use of HTML smuggling to deliver malware.
18 August 2020
Four Ways to Mitigate Supply Chain Security Risks From Ripple20
Enterprises can significantly alleviate current and long-standing third-party risk by using tactical and strategic efforts to assess and manage them.18 August 2020
