Cybersecurity News
BazaLoader Masquerades as Movie-Streaming Service
 The website for “BravoMovies” features fake movie posters and a FAQ with a rigged Excel spreadsheet for “cancelling” the service, but all it downloads is malware.
The website for “BravoMovies” features fake movie posters and a FAQ with a rigged Excel spreadsheet for “cancelling” the service, but all it downloads is malware.
26 May 2021
Bug Bounties and the Cobra Effect
Are bug bounty programs allowing software companies to skirt their responsibility to make better, more secure products from the get-go?26 May 2021
How Are Cyber Insurance Companies Assessing Ransomware Risk?
 From limiting claims payments to tying payments to policyholders' actions, the cyber insurance industry is in "a very dynamic place right now," says Corvus Insurance CEO Phil Edmundson.
From limiting claims payments to tying payments to policyholders' actions, the cyber insurance industry is in "a very dynamic place right now," says Corvus Insurance CEO Phil Edmundson.
26 May 2021
Devo: SIEM Continues to Evolve with Tech Trends and Emerging Threats
SPONSORED: WATCH NOW -- Some organizations split the difference with a hybrid of premises- and cloud-based SIEM, says Ted Julian, senior VP of product at Devo. As security data volumes continue to increase, SIEM's evolution will only continue.26 May 2021
Messaging Apps: The Latest Hotbed in the Fraud Ecosystem
Telegram and other secure messaging apps have become a haven for professional criminals to wreak havoc and turn a profit.26 May 2021
New Iranian Threat Actor Using Ransomware, Wipers in Destructive Attacks
The Agrius group's focus appears to be Israel and the Middle East.26 May 2021
‘Privateer’ Threat Actors Emerge from Cybercrime Swamp
 ‘Privateers’ aren’t necessarily state-sponsored, but they have some form of government protection while promoting their own financially-motivated criminal agenda, according to Cisco Talos.
‘Privateers’ aren’t necessarily state-sponsored, but they have some form of government protection while promoting their own financially-motivated criminal agenda, according to Cisco Talos.
26 May 2021
A Peek Inside the Underground Ransomware Economy
 Threat hunters weigh in on how the business of ransomware, the complex relationships between cybercriminals, and how they work together and hawk their wares on the Dark Web.
Threat hunters weigh in on how the business of ransomware, the complex relationships between cybercriminals, and how they work together and hawk their wares on the Dark Web.
26 May 2021
Orange: Your Leaky Security is Coming from Inside the House!
SPONSORED: Your home WiFi router may be screaming fast, but it's also a major point of vulnerability in this work-from-home era, says Charl van der Walt, head of security research at Orange Cyberdefense. And while Zero Trust offers some relief, he offers up some how-to advice to ensure it's properly deployed.26 May 2021
Bluetooth bugs open the door for attackers to impersonate devices
Devices supporting the Bluetooth Core and Mesh specifications are impacted.26 May 2021
Russian national jailed for running stolen data, hijacked account seller platform deer.io
Kirill Victorovich Firsov was arrested by the FBI last year.26 May 2021
CEO Fraud
CEO Fraud / BEC is a type of targeted email attack. It commonly involves a cyber criminal pretending to be your boss or a senior leader and then tricking you into sending the criminal highly sensitive information, buying gift cards or initiating a wire transfer. Be highly suspicious of any emails demanding immediate action and/or asking you to bypass any security procedures.26 May 2021
Cloud Compromise Costs Organizations $6.2M Per Year
Organizations reported an average of 19 cloud-based compromises in the past year, but most don't evaluate the security of SaaS apps before deployment.25 May 2021
Russia Profiting from Massive Hydra Cybercrime Marketplace
An analysis of Bitcoin transactions from the Hydra marketplace show that the operators are locking sellers into Russian exchanges, likely fueling profits for local actors.25 May 2021
Rise in Opportunistic Hacks and Info-Sharing Imperil Industrial Networks
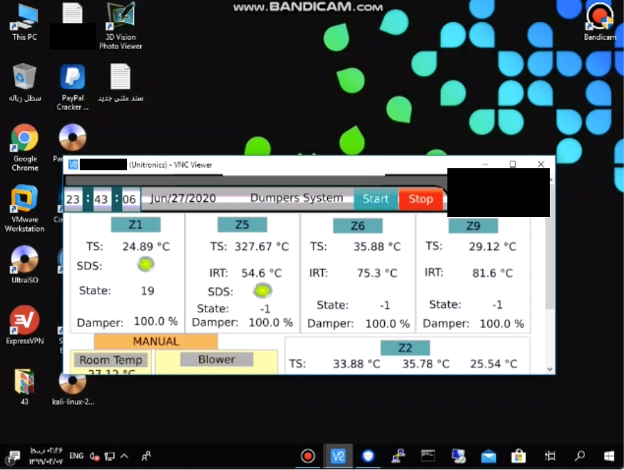 Security researchers at Mandiant have seen an increasing wave of relatively simplistic attacks involving ICS systems - and attackers sharing their finds with one another - since 2020.
Security researchers at Mandiant have seen an increasing wave of relatively simplistic attacks involving ICS systems - and attackers sharing their finds with one another - since 2020.
25 May 2021
Threat Actor ‘Agrius’ Emerges to Launch Wiper Attacks Against Israeli Targets
 The group is using ransomware intended to make its espionage and destruction efforts appear financially motivated.
The group is using ransomware intended to make its espionage and destruction efforts appear financially motivated.
25 May 2021
MacOS Zero-Day Let Attackers Bypass Privacy Preferences
Apple has released security patches for vulnerabilities in macOS and tvOS that reports indicate have been exploited in the wild.25 May 2021
Axis Fosters Work-From-Home Momentum with Zero Trust Network Access
SPONSORED: Watch now -- VPN and VDI, while still useful, lack the hardened security required to keep users secure. That's created an opening for Zero Trust network access.25 May 2021
Russian Sentenced to 30 Months for Running Criminal Website
FBI says sales from illicit online shop deer.io exceeded $17 million25 May 2021
Your Network's Smallest Cracks Are Now Its Biggest Threats
Bad actors have flipped the script by concentrating more on low-risk threats. Here's how to address the threat and the tactics.25 May 2021
