Cybersecurity News
TeamViewer Flaw in Windows App Allows Password-Cracking
 Remote, unauthenticated attackers could exploit the TeamViewer flaw to execute code and crack victims' passwords.
Remote, unauthenticated attackers could exploit the TeamViewer flaw to execute code and crack victims' passwords.
10 August 2020
Black Hat 2020: Fixing voting – boiling the ocean?
With the big voting day rapidly approaching, can the security of the election still be shored up? If so, how?
The post Black Hat 2020: Fixing voting – boiling the ocean? appeared first on WeLiveSecurity
10 August 2020
Vulnerability Prioritization: Are You Getting It Right?
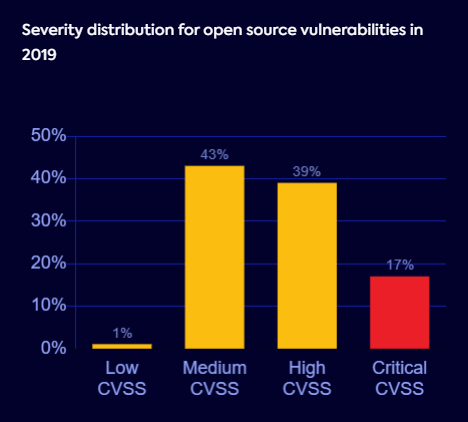 Developers must find a way to zero in on the security vulns that present the most risk and quickly address them without slowing down the pace of development.
Developers must find a way to zero in on the security vulns that present the most risk and quickly address them without slowing down the pace of development.
10 August 2020
Have I Been Pwned to release code base to the open source community
Troy Hunt has made the decision following an unsuccessful attempt to have the platform acquired.10 August 2020
FBI says an Iranian hacking group is attacking F5 networking devices
Sources: Attacks linked to a hacker group known as Fox Kitten (or Parasite), considered Iran's "spear tip" when it comes to cyber-attacks.09 August 2020
Bank of England paid £3m in 'golden goodbyes' over 15 months

Rise in settlements in 2019 included those paid to departing tech security staff shortly before major breach
The Bank of England paid departing staff almost £3m in “golden goodbyes” over 15 months, at the same time as an exodus of workers from its information security team.
Settlement payments to former staff surged to £2.3m in 2019, according to data provided to the Guardian under freedom of information laws. The Bank confirmed that former information security staff received some of the payments.
Continue reading...09 August 2020
China is now blocking all encrypted HTTPS traffic using TLS 1.3 and ESNI
Block was put in place at the end of July and is enforced via China's Great Firewall internet surveillance technology.08 August 2020
Digital Clones Could Cause Problems for Identity Systems
Three fundamental technologies -- chatbots, audio fakes, and deepfake videos -- have improved to the point that creating digital, real-time clones of people is merely a matter of integrating the systems.08 August 2020
DEF CON: New tool brings back 'domain fronting' as 'domain hiding'
After Amazon and Google stopped supporting the censorship-evading domain fronting technique on their clouds in 2018, new Noctilucent toolkit aims to bring it back in a new form as "domain hiding."08 August 2020
Qualcomm Bugs Open 40 Percent of Android Handsets to Attack
 Researchers identified serious flaws in Qualcomm’s Snapdragon SoC and the Hexagon architecture that impacts nearly half of Android handsets.
Researchers identified serious flaws in Qualcomm’s Snapdragon SoC and the Hexagon architecture that impacts nearly half of Android handsets.
07 August 2020
Reddit Attack Defaces Dozens of Channels
The attack has defaced the channels with images and content supporting Donald Trump.07 August 2020
Hacking the PLC via Its Engineering Software
Researcher will demonstrate at DEF CON an emerging threat to industrial control networks.07 August 2020
Attackers Horn in on MFA Bypass Options for Account Takeovers
 Legacy applications don't support modern authentication -- and cybercriminals know this.
Legacy applications don't support modern authentication -- and cybercriminals know this.
07 August 2020
400+ Qualcomm Chip Vulnerabilities Threaten Millions of Android Phones
Security researchers found hundreds of pieces of vulnerable code in the Qualcomm Snapdragon chips powering Android phones.07 August 2020
Have I Been Pwned Set to Go Open-Source
 Fully opening the door to allow people to contribute to – and notably, tinker with – the code for the data-breach information service will be an entirely next-level effort, according to founder Troy Hunt.
Fully opening the door to allow people to contribute to – and notably, tinker with – the code for the data-breach information service will be an entirely next-level effort, according to founder Troy Hunt.
07 August 2020
Hackers are defacing Reddit with pro-Trump messages
BREAKING: Massive hack hits Reddit.07 August 2020
Researcher Finds New Office Macro Attacks for MacOS
Building successful macro attacks means getting past several layers of security, but a Black Hat speaker found a way through.07 August 2020
BEC Campaigns Target Financial Execs via Office 365
A series of business email compromise campaigns has been targeting executives of more than 1,000 companies, most recently in the US and Canada.07 August 2020
Bulgarian police arrest hacker Instakilla
Hacker accused of hacking and extorting companies, selling stolen data online.07 August 2020
Facebook open-sources one of Instagram's security tools
In the first half of 2020, Pysa detected 44% of all security bugs in Instagram's server-side Python code.07 August 2020
