Cybersecurity News
Researchers Connect Complex Specs to Software Vulnerabilities
Following their release of 70 different vulnerabilities in different implementations of TCP/IP stacks over the past year, two companies find a common link.F5 Big-IP Vulnerable to Security-Bypass Bug
 The KDC-spoofing flaw tracked as CVE-2021-23008 can be used to bypass Kerberos security and sign into the Big-IP Access Policy Manager or admin console.
The KDC-spoofing flaw tracked as CVE-2021-23008 can be used to bypass Kerberos security and sign into the Big-IP Access Policy Manager or admin console.
API Hole on Experian Partner Site Exposes Credit Scores
Student researcher is concerned security gap may exist on many other sites.New Terminal Software Module Introduced in PCI Secure Software Standard Version 1.1
Today, the PCI Security Standards Council (PCI SSC) published version 1.1 of the PCI Secure Software Standard and its supporting program documentation. The PCI Secure Software Standard is one of two standards that are part of the PCI Software Security Framework (SSF). The PCI Secure Software requirements provide assurance that payment software is designed, engineered, developed and maintained in a manner that protects payment transactions and data, minimizes vulnerabilities, and defends itself from attacks.
'BadAlloc' Flaws Could Threaten IoT and OT Devices: Microsoft
More than 25 critical memory allocation bugs could enable attackers to bypass security controls in industrial, medical, and enterprise devices.Experian API Leaks Most Americans’ Credit Scores
 Researchers fear wider exposure, amidst a tepid response from Experian.
Researchers fear wider exposure, amidst a tepid response from Experian.
People with dyslexia have skills that we need, says GCHQ

UK surveillance agency says it has long valued neuro-diverse analysts – including Alan Turing
Apprentices on GCHQ’s scheme are four times more likely to have dyslexia than those on other organisations’ programmes, the agency has said, the result of a drive to recruit those whose brains process information differently.
GCHQ says those with dyslexia have valuable skills spotting patterns that others miss – a key area the spy agency wants to encourage as it pivots away from dead letter drops and bugging towards high-tech cybersecurity and data analysis.
Related: GCHQ releases 'most difficult puzzle ever' in honour of Alan Turing
Continue reading...Multi-Gov Task Force Plans to Take Down the Ransomware Economy
 A coalition of 60 global entities (including the DoJ) has proposed a sweeping plan to hunt down and disrupt ransomware gangs by going after their financial operations.
A coalition of 60 global entities (including the DoJ) has proposed a sweeping plan to hunt down and disrupt ransomware gangs by going after their financial operations.
Your Digital Identity's Evil Shadow
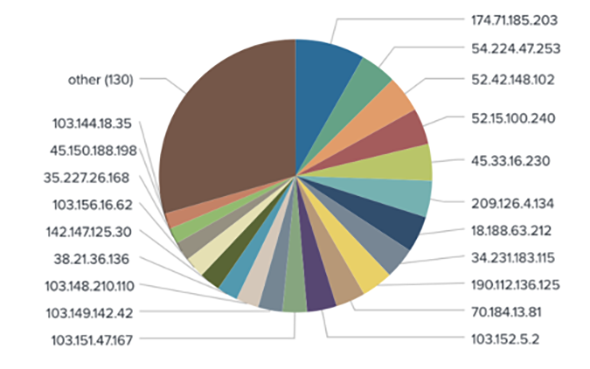 In the wrong hands, these shady shadows are stealthy means to bypass security systems by hiding behind a proxy with legitimate IP addresses and user agents.
In the wrong hands, these shady shadows are stealthy means to bypass security systems by hiding behind a proxy with legitimate IP addresses and user agents.
COVID-19 Results for 25% of Wyoming Accidentally Posted Online
 Sorry, we’ve upchucked your COVID test results and other medical and personal data into public GitHub storage buckets, the Wyoming Department of Health said.
Sorry, we’ve upchucked your COVID test results and other medical and personal data into public GitHub storage buckets, the Wyoming Department of Health said.
The Challenge of Securing Non-People Identities
Non-people identities, which can act intelligently and make decisions on behalf of a person's identity, are a growing cybersecurity risk.FBI teams up with ‘Have I Been Pwned’ to alert Emotet victims
The data breach notification site now allows you to check if your login credentials may have been compromised by Emotet
The post FBI teams up with ‘Have I Been Pwned’ to alert Emotet victims appeared first on WeLiveSecurity
Anti-Vaxxer Hijacks QR Codes at COVID-19 Check-In Sites
 The perp faces jail time, but the incident highlights the growing cyber-abuse of QR codes.
The perp faces jail time, but the incident highlights the growing cyber-abuse of QR codes.
SaaS Attacks: Lessons from Real-Life Misconfiguration Exploits
 There is a way to protect users from deceptive OAuth apps, misconfigurations and misappropriated user permissions. SaaS Security Posture Management (SSPM) takes an automated approach to tracking, and even remediating, the exploitable misconfigurations in organizations’ SaaS apps.
There is a way to protect users from deceptive OAuth apps, misconfigurations and misappropriated user permissions. SaaS Security Posture Management (SSPM) takes an automated approach to tracking, and even remediating, the exploitable misconfigurations in organizations’ SaaS apps.
Task Force Seeks to Disrupt Ransomware Payments
Some of the world's top tech firms are backing a new industry task force focused on disrupting cybercriminal ransomware gangs by limiting their ability to get paid, and targeting the individuals and finances of the organized thieves behind these crimes.DoppelPaymer Gang Leaks Files from Illinois AG After Ransom Negotiations Break Down
 Information stolen in April 10 ransomware attack was posted on a dark web portal and includes private documents not published as part of public records.
Information stolen in April 10 ransomware attack was posted on a dark web portal and includes private documents not published as part of public records.
Paleohacks data leak exposes customer records, password reset tokens
The leak wasn’t dealt with until Amazon was contacted directly.RotaJakiro: A Linux backdoor that has flown under the radar for years
The malware remains undetected by most VirusTotal engines.Prime targets: Governments shouldn’t go it alone on cybersecurity
A year into the pandemic, ESET reveals new research into activities of the LuckyMouse APT group and considers how governments can rise to the cybersecurity challenges of the accelerated shift to digital
The post Prime targets: Governments shouldn’t go it alone on cybersecurity appeared first on WeLiveSecurity