Cybersecurity News
Rapid7 source code, alert data accessed in Codecov supply chain attack
The breached source code subset was used for internal tooling.14 May 2021
Personalized Scams
Cyber criminals now have a wealth of information on almost all of us. With so many organizations getting hacked, cyber criminals simply purchase databases with personal information on millions of people, then use that information to customize their attacks, making them far more realistic. Just because an urgent email has your home address, phone number, or birth date in it does not mean it is legitimate.14 May 2021
Software, Incident Response Among Big Focus Areas in Biden's Cybersecurity Executive Order
Overall objectives are good, but EO may be too prescriptive in parts, industry experts say.13 May 2021
85% of Data Breaches Involve Human Interaction: Verizon DBIR
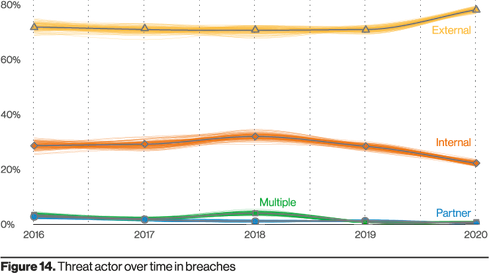 Ransomware, phishing, and Web application attacks all increased during a year in which the majority of attacks involved a human element.
Ransomware, phishing, and Web application attacks all increased during a year in which the majority of attacks involved a human element.
13 May 2021
Colonial Pipeline Shells Out $5M in Extortion Payout, Report
 According to news reports, Colonial Pipeline paid the cybergang known as DarkSide the ransom it demanded in return for a decryption key.
According to news reports, Colonial Pipeline paid the cybergang known as DarkSide the ransom it demanded in return for a decryption key.
13 May 2021
Firms Struggle to Secure Multicloud Misconfigurations
Half of companies had at least one case of having all ports open to the public, while more than a third had an exposed database.13 May 2021
Ransomware Going for $4K on the Cyber-Underground
 An analysis of three popular forums used by ransomware operators reveals a complex ecosystem with many partnerships.
An analysis of three popular forums used by ransomware operators reveals a complex ecosystem with many partnerships.
13 May 2021
Dragos & IronNet Partner on Critical Infrastructure Security
The IT and OT security providers will integrate solutions aimed at improving critical infrastructure security13 May 2021
HelpSystems expands email, cloud security portfolio with acquisition of Agari, Beyond Security
The vendor is targeting areas ripe for growth in the cybersecurity field.13 May 2021
When AI Becomes the Hacker
 Bruce Schneier explores the potential dangers of artificial intelligence (AI) systems gone rogue in society.
Bruce Schneier explores the potential dangers of artificial intelligence (AI) systems gone rogue in society.
13 May 2021
Microsoft Adds GPS Location to Identity & Access Control in Azure AD
New capabilities let admins restrict access to resources from privileged access workstations or regions based on GPS location.13 May 2021
Adapting to the Security Threat of Climate Change
Business continuity plans that address natural and manmade disasters can help turn a cataclysmic business event into a minor slowdown.13 May 2021
European police bust major online investment fraud ring
The operation was carried out against an organized group that used online trading platforms to swindle victims out of US$36 million
The post European police bust major online investment fraud ring appeared first on WeLiveSecurity
13 May 2021
Beyond MFA: Rethinking the Authentication Key
 Tony Lauro, director of security technology and strategy at Akamai, discusses hardware security dongles and using phones to act as surrogates for them.
Tony Lauro, director of security technology and strategy at Akamai, discusses hardware security dongles and using phones to act as surrogates for them.
13 May 2021
Fresh Loader Targets Aviation Victims with Spy RATs
 The campaign is harvesting screenshots, keystrokes, credentials, webcam feeds, browser and clipboard data and more, with RevengeRAT or AsyncRAT payloads.
The campaign is harvesting screenshots, keystrokes, credentials, webcam feeds, browser and clipboard data and more, with RevengeRAT or AsyncRAT payloads.
13 May 2021
Colonial Pipeline paid close to $5 million in ransomware blackmail payment
The payment was reportedly made soon after the attack began. It wasn’t enough to stop the disruption.13 May 2021
Defending the Castle: How World History Can Teach Cybersecurity a Lesson
 Cybersecurity attackers follow the same principles practiced in warfare for millennia. They show up in unexpected places, seeking out portions of an organization's attack surface that are largely unmonitored and undefended.
Cybersecurity attackers follow the same principles practiced in warfare for millennia. They show up in unexpected places, seeking out portions of an organization's attack surface that are largely unmonitored and undefended.
13 May 2021
Apple’s ‘Find My’ Network Exploited via Bluetooth
 The ‘Send My’ exploit can use Apple's locator service to collect and send information from nearby devices for later upload to iCloud servers.
The ‘Send My’ exploit can use Apple's locator service to collect and send information from nearby devices for later upload to iCloud servers.
13 May 2021
Five Critical Password Security Rules Your Employees Are Ignoring
 According to Keeper Security’s Workplace Password Malpractice Report, many remote workers aren’t following best practices for password security.
According to Keeper Security’s Workplace Password Malpractice Report, many remote workers aren’t following best practices for password security.
13 May 2021
Verizon DBIR 2021: "Winners" No Surprise, But All-round Vigilance Essential
Verizon's Data Breach Investigations Report (DBIR) covers 2020 -- a year like no other. Phishing, ransomware, and innovation caused big problems.13 May 2021
