Cybersecurity News
Go SMS Pro Messaging App Exposed Users' Private Media Files
The popular Android app uses easily guessable Web addresses when users send private photos, videos, and voice messages.19 November 2020
Facebook Messenger bug could have allowed hackers to spy on users
The now-patched Messenger bug could have allowed callers to connect audio calls without the callee's knowledge or approval.19 November 2020
GO SMS Pro Android App Exposes Private Photos, Videos and Messages
 The vulnerable version of the app, which has 100 million users, uses easily predictable URLs to link to private content.
The vulnerable version of the app, which has 100 million users, uses easily predictable URLs to link to private content.
19 November 2020
Tis’ the Season for Online Holiday Shopping; and Phishing
 Watch out for these top phishing approaches this holiday season.
Watch out for these top phishing approaches this holiday season.
19 November 2020
The Yellow Brick Road to Risk Management
Beginning the journey to risk management can be daunting, but protecting your business is worth every step.19 November 2020
Code42 Incydr Series: Protect IP with Code42 Incydr
 The Code42 Incydr data risk detection and response solution focuses on giving security teams simplicity, signal and speed.
The Code42 Incydr data risk detection and response solution focuses on giving security teams simplicity, signal and speed.
19 November 2020
Food-Supply Giant Americold Admits Cyberattack
 A reported ransomware attack took down operations at the company, which in talks for COVID-19 vaccine-distribution contracts.
A reported ransomware attack took down operations at the company, which in talks for COVID-19 vaccine-distribution contracts.
19 November 2020
IoT Cybersecurity Improvement Act Passed, Heads to President’s Desk
 Security experts praised the newly approved IoT law as a step in the right direction for insecure connected federal devices.
Security experts praised the newly approved IoT law as a step in the right direction for insecure connected federal devices.
19 November 2020
New Proposed DNS Security Features Released
Verisign's R&D team has developed new ways to authenticate and optimize DNS traffic on the client side of the domain-name resolution process.19 November 2020
LidarPhone attack converts smart vacuums into microphones
LidarPhone attack works by converting a smart vacuum's LiDAR navigational component into a laser microphone.19 November 2020
Payment Security in India: 2020 India Forum
As Associate Director for India, Nitin Bhatnagar is responsible for driving awareness and adoption of PCI Security Standards in the country. Bhatnagar works closely with merchants, acquirers, financial institutions, security practitioners, law enforcement and other key stakeholders across the Indian payment ecosystem. Here he discusses payment security challenges and opportunities in India and the second annual PCI SSC India Forum planned for 9 December online
19 November 2020
2021 Cybersecurity Spending: How to Maximize Value
This is a pivotal moment for CISOs. As their influence increases, so does the pressure for them to make the right decisions.19 November 2020
APT Exploits Microsoft Zerologon Bug: Targets Japanese Companies
 Threat actors mount year-long campaign of espionage, exfiltrating data, stealing credentials and installing backdoors on victims’ networks.
Threat actors mount year-long campaign of espionage, exfiltrating data, stealing credentials and installing backdoors on victims’ networks.
19 November 2020
The worst passwords of 2020: Is it time to change yours?
They’re supremely easy to remember, as well as easy to crack. Here’s how to improve your password security.
The post The worst passwords of 2020: Is it time to change yours? appeared first on WeLiveSecurity
19 November 2020
Unpatched Browsers Abound, Study Shows
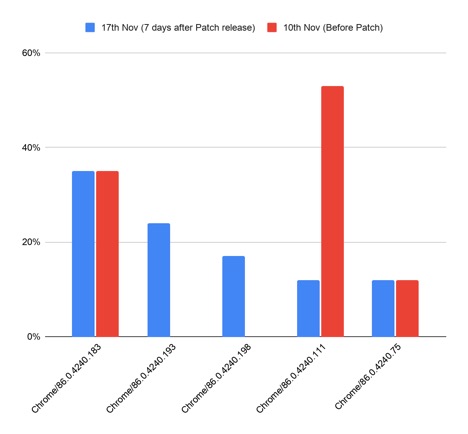 Google Chrome users don't always take time to relaunch browser updates, and some legacy applications don't support new versions of Chrome, Menlo Security says.
Google Chrome users don't always take time to relaunch browser updates, and some legacy applications don't support new versions of Chrome, Menlo Security says.
19 November 2020
Cybercriminals Batter Automakers With Ransomware, IP Theft Cyberattacks
 While the industry focus is on vehicle hacking, when it comes to the automotive industry cybercriminals are opting for less complex and sophisticated attacks - from phishing to ransomware.
While the industry focus is on vehicle hacking, when it comes to the automotive industry cybercriminals are opting for less complex and sophisticated attacks - from phishing to ransomware.
19 November 2020
New Grelos skimmer variant reveals overlap in Magecart group activities, malware infrastructure
The discovery of a new skimmer variant reveals the difficulties associated with tracking separate Magecart campaigns.19 November 2020
Fearing drama, Mozilla opens public consultation before worldwide Firefox DoH rollout
Mozilla wants to enable DNS-over-HTTPS (DoH) in Firefox for all users worldwide, but wants to hear from ISPs, governments, and companies beforehand.19 November 2020
Online Shopping Surge Puts Focus on Consumer Security Habits
Companies will have to tread a fine line between delivering security and a frictionless shopping experience, security firms say.18 November 2020
Cisco Webex Vulns Let 'Ghost' Attendees Spy on Meetings
Three vulnerabilities, patched today, could let an attacker snoop on meetings undetected after the host removes them.18 November 2020

