Cybersecurity News
Child tweets on behalf of nuke, space mission agency US Strategic Command
The gibberish tweet left some amused, some concerned that the account had been compromised.31 March 2021
VMware patches critical vRealize Operations platform vulnerabilities
Administrator credentials could be stolen by exploiting the bugs.31 March 2021
Are you prepared to prevent data loss?
From losing cherished memories to missing deadlines, the impact of not having backups when a data disaster strikes can hardly be overstated
The post Are you prepared to prevent data loss? appeared first on WeLiveSecurity
31 March 2021
Pandemic threats: The common threads in COVID-19 scams and criminal schemes
Researchers explore how cybercriminals have exploited the coronavirus pandemic over the past year.31 March 2021
Whistleblower claims Ubiquiti Networks data breach was ‘catastrophic’
The source alleges the January security incident was severely downplayed.31 March 2021
Publicly Available Data Enables Enterprise Cyberattacks
Adversaries scour social media platforms and use other tactics to gather information that facilitates targeted enterprise attacks, research shows.30 March 2021
Security on a Shoestring? More Budget Means More Detection
Companies that spend the smallest share of their IT budget on security see fewer threats, but that's not good news.30 March 2021
What We Know (and Don't Know) So Far About the 'Supernova' SolarWinds Attack
A look at the second elusive attack targeting SolarWinds software that researchers at Secureworks recently cited as the handiwork of Chinese nation-state hackers.30 March 2021
Ziggy Ransomware Gang Offers Refunds to Victims
 Ziggy joins Fonix ransomware group and shuts down, with apologies to targets.
Ziggy joins Fonix ransomware group and shuts down, with apologies to targets.
30 March 2021
Malicious Docker Cryptomining Images Rack Up 20M Downloads
 Publicly available cloud images are spreading Monero-mining malware to unsuspecting cloud developers.
Publicly available cloud images are spreading Monero-mining malware to unsuspecting cloud developers.
30 March 2021
White Ops Renames Company 'Human'
The company first confirmed plans to change its name in October 2020.30 March 2021
Reduced Certification Requirements for PA-QSA Secure Software Assessor Candidates until 30 June 2021
When the Payment Application Data Security Standard (PA-DSS) v3.2 closes on 28 October 2022, it will be superseded by the Secure Software Standard and Program, which is part of the PCI Software Security Framework (SSF).
30 March 2021
Whistleblower: Ubiquiti Breach “Catastrophic”
On Jan. 11, Ubiquiti Inc. [NYSE:UI] — a major vendor of cloud-enabled Internet of Things (IoT) devices such as routers, network video recorders and security cameras — disclosed that a breach involving a third-party cloud provider had exposed customer account credentials. Now a source who participated in the incident response to that breach alleges Ubiquiti massively downplayed a “catastrophic” incident to minimize the hit to its stock price, and that the third-party cloud provider claim was a fabrication.30 March 2021
What You Need to Know -- or Remember -- About Web Shells
 What's old is new again as Web shell malware becomes the latest attack vector in widespread Exchange exploits. Here's a primer on what Web shells are and what they do.
What's old is new again as Web shell malware becomes the latest attack vector in widespread Exchange exploits. Here's a primer on what Web shells are and what they do.
30 March 2021
Watch Out for These Cyber-Risks
It's difficult to predict what will materialize in the months ahead in terms of cyber-risks, which is why it's wise to review your organization's security posture now.30 March 2021
What You Need to Know -- or Remember -- About Web Shells
 What's old is new again as Web shell malware becomes the latest attack vector in widespread Exchange exploits. Here's a primer on what Web shells are and what they do.
What's old is new again as Web shell malware becomes the latest attack vector in widespread Exchange exploits. Here's a primer on what Web shells are and what they do.
30 March 2021
SolarWinds Attackers Accessed DHS Emails, Report
 Current and former administration sources say the nation-state attackers were able to read the Homeland Security Secretary's emails, among others.
Current and former administration sources say the nation-state attackers were able to read the Homeland Security Secretary's emails, among others.
30 March 2021
Ghost Users Haunt Healthcare Firms
Data security hygiene severely lacking among healthcare firms, new research shows.30 March 2021
Backdoor added to PHP source code in Git server breach
Had the incident gone unnoticed, the attackers could have taken over websites using the tainted code
The post Backdoor added to PHP source code in Git server breach appeared first on WeLiveSecurity
30 March 2021
Beyond MITRE ATT&CK: The Case for a New Cyber Kill Chain
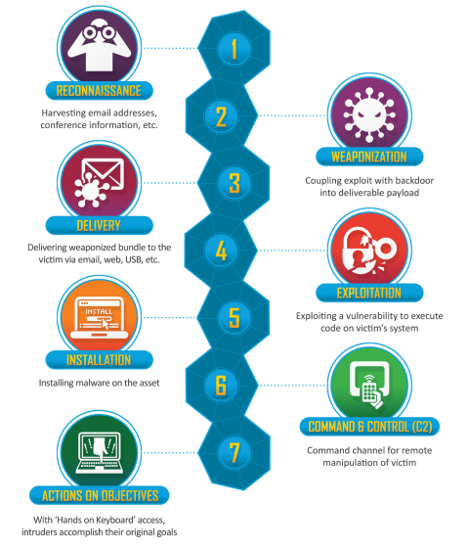 The Cyber Kill Chain and MITRE ATT&CK are popular reference frameworks to analyze breaches, but amid the rise of XDR, we may need a new one.
The Cyber Kill Chain and MITRE ATT&CK are popular reference frameworks to analyze breaches, but amid the rise of XDR, we may need a new one.
30 March 2021

