Cybersecurity News
International sting takes down online marketplace of stolen identities
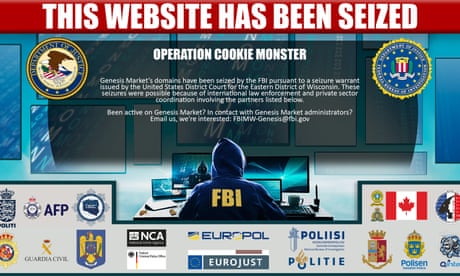
Operation led by FBI and Dutch police with involvement of UK National Crime Agency takes Genesis Market offline
A criminal online marketplace selling millions of stolen identities for as little as 56p has been taken down in an international crackdown.
The sting, led by the FBI and Dutch police with the involvement of law enforcement agencies across 18 countries, including the UK’s National Crime Agency (NCA), took Genesis Market offline on Tuesday evening.
Continue reading...Why you should spring clean your home network and audit your backups
Do you know how many devices are connected to your home network? You don’t? This is precisely why it’s time for a network audit.
The post Why you should spring clean your home network and audit your backups appeared first on WeLiveSecurity
FBI Seizes Bot Shop ‘Genesis Market’ Amid Arrests Targeting Operators, Suppliers
Several domain names tied to Genesis Market, a bustling cybercrime store that sold access to passwords and other data stolen from millions of computers infected with malicious software, were seized by the Federal Bureau of Investigation (FBI) today. Sources tell KrebsOnsecurity the domain seizures coincided with "dozens" of arrests in the United States and abroad targeting those who allegedly operated the service, as well as suppliers who continuously fed Genesis Market with freshly-stolen data.Request for Comments: PCI P2PE v3.1 Standard
P2PE Assessors, P2PE Application Assessors, Qualified PIN Assessors, Qualified Security Assessors, and Participating Organizations are invited to provide feedback on the currently published P2PE v3.1 Standard during a 30-day request for comments (RFC) period running from 4 Apr 2023 through 4 May 2023.
Paving the Way: Inspiring Women in Payments - A Q&A featuring Nancy Zayed
Nancy Zayed recognizes that there is a significant underrepresentation of women in science, technology, engineering, and math (STEM) professions with a variety of factors contributing to this imbalance. But, as the cofounder and Chief Technology Officer of her own software payment security company, she chose not to be influenced by these facts and instead became an example of how women can achieve success in these industries. In this edition of our blog, Nancy discusses why we need to keep reminding ourselves that women have always affected this industry and that they actually lead innovation. She believes that knowing women’s role in the history of technology will propel their future.
Spring into action and tidy up your digital life like a pro
Spring is in the air and as the leaves start growing again, why not breathe some new life into the devices you depend on so badly?
The post Spring into action and tidy up your digital life like a pro appeared first on WeLiveSecurity
A Serial Tech Investment Scammer Takes Up Coding?
John Clifton Davies, a 60-year-old con man from the United Kingdom who fled the country in 2015 before being sentenced to 12 years in prison for fraud, has enjoyed a successful life abroad swindling technology startups by pretending to be a billionaire investor. Davies' newest invention appears to be "CodesToYou," which purports to be a "full cycle software development company" based in the U.K.German Police Raid DDoS-Friendly Host ‘FlyHosting’
Authorities in Germany this week seized Internet servers that powered FlyHosting, a dark web service that catered to cybercriminals operating DDoS-for-hire services. Fly Hosting first advertised on cybercrime forums in November 2022, saying it was a Germany-based hosting firm that was open for business to anyone looking for a reliable place to host malware, botnet controllers, or DDoS-for-hire infrastructure.Avoiding data backup failures – Week in security with Tony Anscombe
Today is World Backup Day, but maybe we also need a "did you test your backups" day?
The post Avoiding data backup failures – Week in security with Tony Anscombe appeared first on WeLiveSecurity
World Backup Day: Avoiding a data disaster is a forever topic
By failing to prepare you are preparing to fail. Make sure you're able to bounce back if, or when, a data disaster strikes.
The post World Backup Day: Avoiding a data disaster is a forever topic appeared first on WeLiveSecurity
Cyberwarfare leaks show Russian army is adopting mindset of secret police

Documents leaked from Vulkan cybersecurity firm also raise questions about role of IT engineers behind information-control project
A consortium of media outlets have published a bombshell investigation about Russia’s cyber-capabilities, based on a rare leak of documents. The files come from NTC Vulkan, a cybersecurity firm in Moscow that doubles as a contractor to Russian military and intelligence agencies.
They reveal how, for years, a group of top Russian IT engineers have been hired to work with Russian military intelligence and a research facility of the FSB, Vladimir Putin’s domestic spy agency. This might seem an unusual mix, and would have been unimaginable before the end of the cold war.
Continue reading...‘Vulkan files’ leak reveals Putin’s global and domestic cyberwarfare tactics

• Documents leaked by whistleblower angry over Ukraine war
• Private Moscow consultancy bolstering Russian cyberwarfare
• Tools support hacking operations and attacks on infrastructure
• Documents linked to notorious Russian hacking group Sandworm
• Russian program aims to control internet and spread disinformation
The inconspicuous office is in Moscow’s north-eastern suburbs. A sign reads: “Business centre”. Nearby are modern residential blocks and a rambling old cemetery, home to ivy-covered war memorials. The area is where Peter the Great once trained his mighty army.
Inside the six-storey building, a new generation is helping Russian military operations. Its weapons are more advanced than those of Peter the Great’s era: not pikes and halberds, but hacking and disinformation tools.
Continue reading...ESET Research Podcast: A year of fighting rockets, soldiers, and wipers in Ukraine
ESET experts share their insights on the cyber-elements of the first year of the war in Ukraine and how a growing number of destructive malware variants tried to rip through critical Ukrainian systems
The post ESET Research Podcast: A year of fighting rockets, soldiers, and wipers in Ukraine appeared first on WeLiveSecurity
Pig butchering scams: The anatomy of a fast‑growing threat
How fraudsters groom their marks and move in for the kill using tricks from the playbooks of romance and investment scammers
The post Pig butchering scams: The anatomy of a fast‑growing threat appeared first on WeLiveSecurity
UK Sets Up Fake Booter Sites To Muddy DDoS Market
The United Kingdom's National Crime Agency (NCA) has been busy setting up phony DDoS-for-hire websites that seek to collect information on users, remind them that launching DDoS attacks is illegal, and generally increase the level of paranoia for people looking to hire such services.How the world is turning against social media

France has banned not only TikTok from government phones, but Facebook and Twitter, too. Could this be a tipping point for big tech? Plus, AI-generated pictures of the pope signal a new type of viral image
Government workers in the UK, US, Canada and European Union (the list will have grown by the time you read this) are banned from installing TikTok on their phones.
On Friday, France joined that list, preventing its civil servants from installing TikTok – and everything else. From the government’s press release (original in French):
After an analysis of the issues, in particular security, the government has decided to ban the downloading and installation of recreational applications on professional telephones provided to public officials from now on.
Recreational applications do not have sufficient levels of cybersecurity and data protection to be deployed on government equipment. This ban applies immediately and uniformly. Exemptions may be granted on an exceptional basis …
Continue reading...Staying safe on OnlyFans: The naked truth
How content creators and subscribers can embrace the social media platform without (overly) exposing themselves to the potentially toxic brew of NSFW content and privacy threats
The post Staying safe on OnlyFans: The naked truth appeared first on WeLiveSecurity
Request for Comments: PCI TSP Security Requirements
From 27 March to 27 April 2023, eligible stakeholders are invited to review and provide feedback on the PCI Token Service Provider (TSP) Security Requirements v1.0 during a 30-day request for comments (RFC) period.
Yes, it’s crazy to have TikTok on official phones. But it’s not good for any of us | John Naughton
 Fears for data security lie behind recent government bans on the Chinese-owned app, but zombie scrolling has health dangers too
Fears for data security lie behind recent government bans on the Chinese-owned app, but zombie scrolling has health dangers tooAs of this moment, government officials in 11 countries are forbidden to run TikTok on their government-issued phones. The countries include the US, Canada, Denmark, Belgium, the UK, New Zealand, Norway, France, the Netherlands and Poland. In addition, European Commission and European parliament staff were required to delete the app. This raises two questions.
First, why were politicians and senior officials in democracies scrolling like zombies through dance crazes, daft pet videos, feeling “bonita” and things you can do with smudged lipstick?
Continue reading...TikTok banned on London City Hall devices over security concerns

Move by Greater London authority comes after Chinese-owned app was blocked on UK parliamentary devices
London City Hall staff will no longer have TikTok on their devices in the latest ban imposed on the Chinese-owned social media app over security concerns.
The Greater London authority (GLA) said the rule was implemented as it takes information security “extremely seriously”.
Continue reading...


