Cybersecurity News
REvil Ransomware Gang Spill Details on US Attacks
 The REvil ransomware gang is interviewed on the Telegram channel called Russian OSINT.
The REvil ransomware gang is interviewed on the Telegram channel called Russian OSINT.
The Perfect Storm for PAM to Grow In
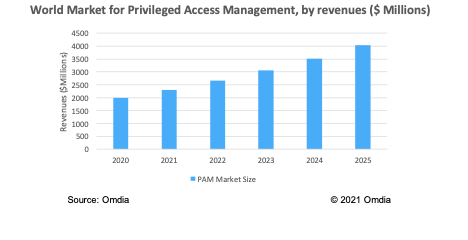 With more staff working remotely, privileged access management (or PAM) has never been more important. Market forecasts, drivers, and trends are explored.
With more staff working remotely, privileged access management (or PAM) has never been more important. Market forecasts, drivers, and trends are explored.
Fake News
Fake news is a false narrative that is published and promoted as if it were true. People (and organizations) create fake news to control and manipulate your thoughts and actions. Be skeptical of what you read on the Internet, use trusted sources that are vetted, check their motivations and funding.Data Breaches Drive Higher Loan Interest Rates
Businesses that suffer a security breach may not see their stock price tumble, but they may pay higher rates for loans and be forced to provide collateral, researchers report.Proposed Sale Casts Cloud Over Future of FireEye's Products
Symphony Technology Group, which is buying FireEye, already owns multiple security companies "with redundancies in numerous areas."‘Battle for the Galaxy’ Mobile Game Leaks 6M Gamer Profiles
 Unprotected server exposes AMT Games user data containing user emails and purchase information.
Unprotected server exposes AMT Games user data containing user emails and purchase information.
Google Experts Explore Open Source Security Challenges & Fixes
An open source security event brought discussions of supply chain security and managing flaws in open source projects.NY & Mass. Transportation Providers Targeted in Recent Attacks
New York's Metropolitan Transportation Authority and the Steamship Authority of Massachusetts were both victims of cyberattacks.REvil Behind JBS Ransomware Attack: FBI
Officials attribute the attack to REvil/Sodinokibi and say they are working to bring the threat actors to justice.Google PPC Ads Used to Deliver Infostealers
 The crooks pay top dollar for Google search results for the popular AnyDesk, Dropbox & Telegram apps that lead to a malicious, infostealer-packed website.
The crooks pay top dollar for Google search results for the popular AnyDesk, Dropbox & Telegram apps that lead to a malicious, infostealer-packed website.
The True Cost of a Ransomware Attack
Companies need to prepare for the costs of an attack now, before they get attacked. Here's a checklist to help.Zero‑day in popular WordPress plugin exploited to take over websites
Websites using Fancy Product Designer are susceptible to remote code execution attacks even if the plugin is deactivated
The post Zero‑day in popular WordPress plugin exploited to take over websites appeared first on WeLiveSecurity
The Colonial Pipeline Attack Is Your Boardroom Wake-Up Call
Why business leaders must adopt a risk-led approach to cybersecurity.Payment Security in India: A Discussion with Stakeholders
The PCI Security Standards Council (PCI SSC) Security Summit of India, an online event took place this week with more than 1,000 payment security practitioners from India discussing the latest in payment security and standards. Here we talk with Nitin Bhatnagar, Associate Director, India, PCI SSC, Rajesh Hariharan, Director, Information Security, Global Payments; Viswanath Krishnamurthy, Chief Risk Officer, National Payments Corporation of India and Swati Sharma, FSI Compliance Specialist, Amazon Internet Service Provider Limited about payment security trends, highlights from the Security Summit of India, and industry involvement opportunities for the region.
Exchange Servers Targeted by ‘Epsilon Red’ Malware
 REvil threat actors may be behind a set of PowerShell scripts developed for encryption and weaponized to exploit vulnerabilities in corporate networks, the ransom note suggests.
REvil threat actors may be behind a set of PowerShell scripts developed for encryption and weaponized to exploit vulnerabilities in corporate networks, the ransom note suggests.
Then and Now: Securing Privileged Access Within Healthcare Orgs
 Joseph Carson, chief security scientist and advisory CISO at ThycoticCentrify, discusses best practices for securing healthcare data against the modern threat landscape.
Joseph Carson, chief security scientist and advisory CISO at ThycoticCentrify, discusses best practices for securing healthcare data against the modern threat landscape.
Necro Python bot revamped with new VMWare, server exploits
The latest version of the bot has also been equipped with a cryptocurrency miner.Chinese cybercriminals spent three years creating a new backdoor to spy on governments
The new tool has been used in ongoing cyberespionage activities.ESET Threat Report T1 2021
A view of the T1 2021 threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and research experts
The post ESET Threat Report T1 2021 appeared first on WeLiveSecurity

