Cybersecurity News
U.S. Gov Agency Targeted With Malware-Laced Emails
 The malicious email campaign included a never-before-seen malware downloader called Carrotball, and may be linked to the Konni Group APT.
The malicious email campaign included a never-before-seen malware downloader called Carrotball, and may be linked to the Konni Group APT.
23 January 2020
Shlayer, No. 1 Threat for Mac, Targets YouTube, Wikipedia
 The malware uses thousands of partner websites to spread malvertising code.
The malware uses thousands of partner websites to spread malvertising code.
23 January 2020
Deconstructing Web Cache Deception Attacks: They're Bad; Now What?
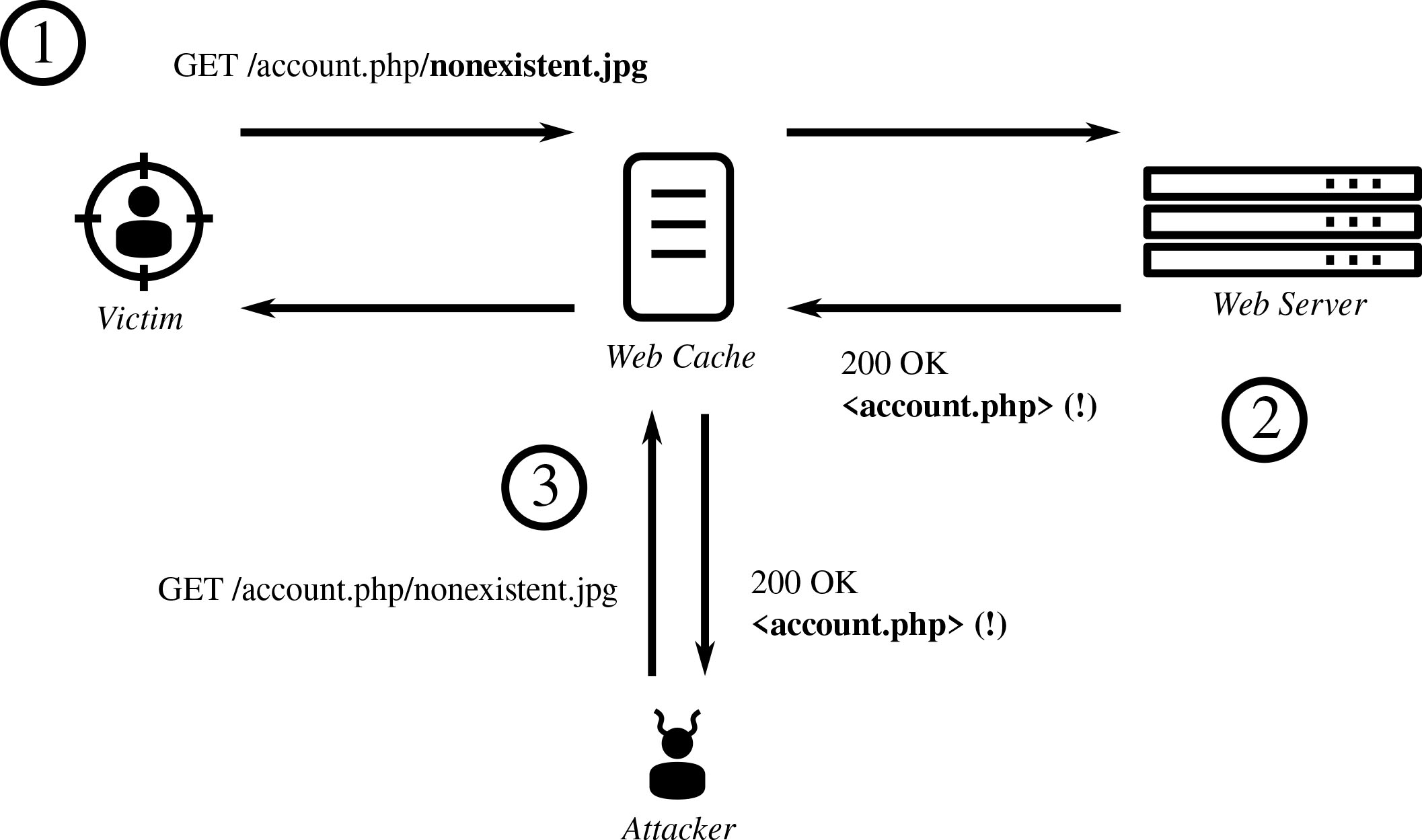 Expect cache attacks to get worse before they get better. The problem is that we don't yet have a good solution.
Expect cache attacks to get worse before they get better. The problem is that we don't yet have a good solution.
23 January 2020
Severe Vulnerabilities Discovered in GE Medical Devices
CISA has released an advisory for six high-severity CVEs for GE Carescape patient monitors, Apex Pro, and Clinical Information Center systems.23 January 2020
MDhex vulnerabilities impact GE patient vital signs monitoring devices
GE Healthcare plans to release patches in Q2 2020.23 January 2020
Someone is uninstalling the Phorpiex malware from infected PCs and telling users to install an antivirus
Malware analysts believe someone has hijacked the Phorpiex botnet from its creator and is sabotaging its operations by alerting users they've been infected.23 January 2020
Cisco Warns of Critical Network Security Tool Flaw
 The critical flaw exists in Cisco's administrative management tool, used with network security solutions like firewalls.
The critical flaw exists in Cisco's administrative management tool, used with network security solutions like firewalls.
23 January 2020
Weathering the Privacy Storm from GDPR to CCPA & PDPA
A general approach to privacy, no matter the regulation, is the only way companies can avoid a data protection disaster in 2020 and beyond.23 January 2020
Ryuk Ransomware Hit Multiple Oil & Gas Facilities, ICS Security Expert Says
Attackers 'weaponized' Active Directory to spread the ransomware.23 January 2020
Microsoft exposed 250 million customer support records
Databases containing 14 years’ worth of customer support logs were publicly accessible with no password protection
The post Microsoft exposed 250 million customer support records appeared first on WeLiveSecurity
23 January 2020
Microsoft exposed 250 million customer support records
Databases containing 14 years’ worth of customer support logs were publicly accessible with no password protection
The post Microsoft exposed 250 million customer support records appeared first on WeLiveSecurity
23 January 2020
Google: Flaws in Apple’s Private-Browsing Technology Allow for Third-Party Tracking
 New research outlines vulnerabilities in Safari’s Intelligent Tracking Protection that can reveal user browsing behavior to third parties.
New research outlines vulnerabilities in Safari’s Intelligent Tracking Protection that can reveal user browsing behavior to third parties.
23 January 2020
To Avoid Disruption, Ransomware Victims Continue to Pay Up
For all the cautions against doing so, one-third of organizations in a Proofpoint survey said they paid their attackers after getting infected with ransomware.23 January 2020
Securely Disposing Mobile Devices
Do you plan on giving away or selling one of your older mobile devices? Make sure you wipe or reset your device before disposing of it. If you don't, the next person who owns it will have access to all of your accounts and personal information.23 January 2020
Pwn2Own Miami Contestants Haul in $180K for Hacking ICS Equipment
 The competition targets the systems that run critical infrastructure and more.
The competition targets the systems that run critical infrastructure and more.
22 January 2020
Apple Addresses iPhone 11 Location Privacy Concern
Apple is rolling out a new update to its iOS operating system that addresses the location privacy issue on iPhone 11 devices that was first detailed here last month.22 January 2020
Vivin Nets Thousands of Dollars Using Cryptomining Malware
 A newly discovered threat actor named Vivin is raking in Monero from cryptomining malware, showing that this type of attack isn't going away anytime soon.
A newly discovered threat actor named Vivin is raking in Monero from cryptomining malware, showing that this type of attack isn't going away anytime soon.
22 January 2020
For Mismanaged SOCs, The Price Is Not Right
New research finds security operations centers suffer high turnover and yield mediocre results for the investment they require.22 January 2020
A timeline of events surrounding the Bezos phone hack
Bezos hack connected to Khashoggi murder and the Washington Post's subsequent media coverage.22 January 2020
Eight Flaws in MSP Software Highlight Potential Ransomware Vector
An attack chain of vulnerabilities in ConnectWise's software for MSPs has similarities to some of the details of the August attack on Texas local and state agencies.22 January 2020
