Cybersecurity News
Facebook Tops Imitated Brands as Attackers Target Tech
Brand impersonators favor Facebook, Yahoo, Network, and PayPal in phishing attempts to steal credentials from victims.06 February 2020
Facebook now lets parents monitor their children’s chats
The feature is part of expanded parental controls on the Messenger Kids app aimed at children under 13
The post Facebook now lets parents monitor their children’s chats appeared first on WeLiveSecurity
06 February 2020
Facebook now lets parents monitor their children’s chats
The feature is part of expanded parental controls on the Messenger Kids app aimed at children under 13
The post Facebook now lets parents monitor their children’s chats appeared first on WeLiveSecurity
06 February 2020
Metamorfo Returns with Keylogger Trick to Target Financial Firms
 The malware uses a tactic to force victims to retype passwords into their systems - which it tracks via a keylogger.
The malware uses a tactic to force victims to retype passwords into their systems - which it tracks via a keylogger.
06 February 2020
U.S. Finance Sector Hit with Targeted Backdoor Campaign
 The powerful Minebridge backdoor gives cyberattackers full run of a victim's machine.
The powerful Minebridge backdoor gives cyberattackers full run of a victim's machine.
06 February 2020
Poll: A Matter of Trust
Has working in the cybersecurity industry affected your ability to trust? Take the poll now.06 February 2020
A Matter of Trust
Has working in the cybersecurity industry affected your ability to trust? Take the poll now.06 February 2020
Invisible Pixel Patterns Can Communicate Data Covertly
University researchers show that changing the brightness of monitor pixels can communicates data from air-gapped systems in a way not visible to human eyes.06 February 2020
How Can We Make Election Technology Secure?
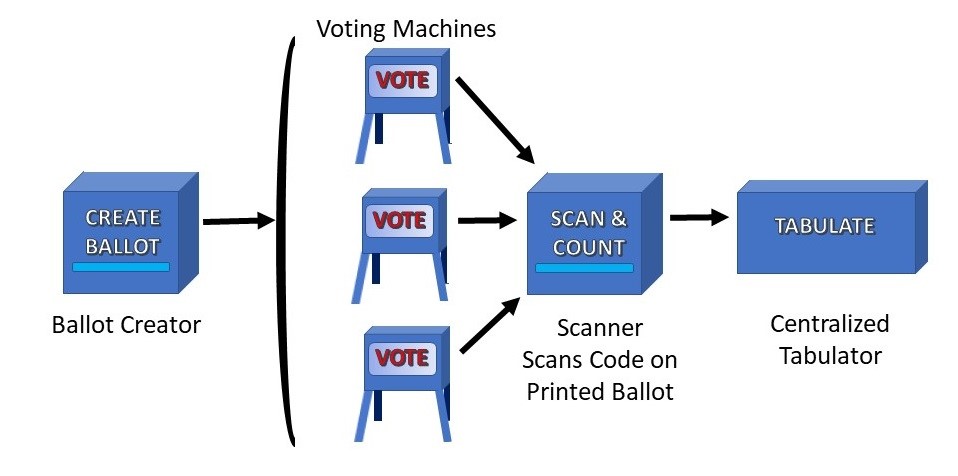 In Iowa this week, a smartphone app for reporting presidential caucus results debuted. It did not go well.
In Iowa this week, a smartphone app for reporting presidential caucus results debuted. It did not go well.
06 February 2020
The RSAC 2020 Trend Report
 What’s trending in cybersecurity? This year’s session submissions tell us.
What’s trending in cybersecurity? This year’s session submissions tell us.
06 February 2020
Dutch court rules AI benefits fraud detection system violates EU human rights
SyRI was used to predict who may be at high risk of conducting housing or social security fraud.06 February 2020
RSAC Sets Finalists for Innovation Sandbox
 The 10 finalists will each have three minutes to make their case for being the most innovative, promising young security company of the year.
The 10 finalists will each have three minutes to make their case for being the most innovative, promising young security company of the year.
06 February 2020
RSAC Sets Finalists for Innovation Sandbox
 The 10 finalists will each have three minutes to make their case for being the most innovative, promising young security company of the year.
The 10 finalists will each have three minutes to make their case for being the most innovative, promising young security company of the year.
06 February 2020
Charming Kitten Uses Fake Interview Requests to Target Public Figures
 APT group poses as a former Wall Street Journal journalist to launch phishing campaigns and steal victim email account details.
APT group poses as a former Wall Street Journal journalist to launch phishing campaigns and steal victim email account details.
06 February 2020
Dropbox Passes $1M Milestone for Bug-Bounty Payouts
 The file-sharing service also disclosed details of past notable bugs for the first time.
The file-sharing service also disclosed details of past notable bugs for the first time.
06 February 2020
Health Share of Oregon discloses data breach, theft of member PII
A break-in and stolen laptop are at the heart of the security incident.06 February 2020
Academics steal data from air-gapped systems using screen brightness variations
Israeli researchers use quick flickers in LCD screen brightness to encode and exfiltrate data.06 February 2020
Vixie: The Unintended Consequences of Internet Privacy Efforts
 Paul Vixie says emerging encryption protocols for endpoints could 'break' security in enterprise - and even home - networks.
Paul Vixie says emerging encryption protocols for endpoints could 'break' security in enterprise - and even home - networks.
05 February 2020
When Your Used Car is a Little Too ‘Mobile’
Many modern vehicles let owners use the Internet or a mobile device to control the car's locks, track location and performance data, and start the engine. But who exactly owns that control is not always clear when these smart cars are sold or leased anew. Here's the story of one former electric vehicle owner who discovered he could still gain remote, online access to his old automobile years after his lease ended.05 February 2020
