Cybersecurity News
Microsoft warns about attacks with the PonyFinal ransomware
PonyFinal infections have been reported in India, Iran, and the US.27 May 2020
Microsoft Shares PonyFinal Threat Data, Warns of Delivery Tactics
PonyFinal is deployed in human-operated ransomware attacks, in which adversaries tailor their techniques based on knowledge of a target system.27 May 2020
Critical Android flaw lets attackers hijack almost any app, steal data
Left unpatched, the vulnerability could expose almost all Android users to the risk of having their personal data intercepted by attackers
The post Critical Android flaw lets attackers hijack almost any app, steal data appeared first on WeLiveSecurity
27 May 2020
OpenSSH to deprecate SHA-1 logins due to security risk
Breaking a SHA-1-generated SSH authentication key now costs roughly $50,000, putting high-profile remote servers at risk of attacks.27 May 2020
What the World's Elite Protectors Teach Us about Cybersecurity
How to protect anyone and anything, from the perspective of a career Secret Service agent and former special operations marine.27 May 2020
6 Steps Consumers Should Take Following a Hack
 Without the luxury of an IT security team to help them after a breach or credit card compromise, consumers will want to keep these tips in mind.
Without the luxury of an IT security team to help them after a breach or credit card compromise, consumers will want to keep these tips in mind.
27 May 2020
Hackers Sell Data from 26 Million LiveJournal Users on Dark Web
 Passwords and other credentials have been listed on Have I Been Pwned as attack rumors circulate.
Passwords and other credentials have been listed on Have I Been Pwned as attack rumors circulate.
27 May 2020
Virtual Black Hat USA Offers Unparalleled Access to Expert Security Insights
Attendees can look forward to the same high-quality Briefings and Trainings from the comfort of their own desk.27 May 2020
Netwalker Ransomware Tools Reveal Attacker Tactics and Techniques
Malware and related files show that ransomware operators don't need a cutting-edge arsenal to be effective.27 May 2020
New fuzzing tool finds 26 USB bugs in Linux, Windows, macOS, and FreeBSD
Eighteen of the 26 bugs impact Linux. Eleven have been patched already.27 May 2020
26 million LiveJournal credentials leaked online, sold on the dark web
LiveJournal credentials were obtained in a 2014 hack, but leaked online earlier this month.26 May 2020
Report: ATM Skimmer Gang Had Protection from Mexican Attorney General’s Office
A group of Romanians operating an ATM company in Mexico and suspected of bribing technicians to install sophisticated Bluetooth-based skimmers in cash machines throughout several top Mexican tourist destinations have enjoyed legal protection from a top anti-corruption official in the Mexican attorney general's office, according to a new complaint filed with the government's internal affairs division.26 May 2020
StrandHogg 2.0 Emerges as 'Evil Twin' to Android Threat
The vulnerability, which exists in almost every version of Android, is both more dangerous and harder to detect than its predecessor.26 May 2020
Americans Care About Security But Don't Follow Through
Most Americans say they're very concerned about online security but still behave in insecure ways, according to a new survey.26 May 2020
StrandHogg 2.0 Critical Bug Allows Android App Hijacking
 a malicious app installed on a device can hide behind legitimate apps.
a malicious app installed on a device can hide behind legitimate apps.
26 May 2020
Turla Backdoor Adds Gmail Web Interface for Command-and-Control
The latest version of ComRAT is another sign of the threat actor's continued focus on targets in the government, military, and other sectors.26 May 2020
How to Pay a Ransom: A Step-By-Step Guide for Something You'd Never Do
 Even prior to the COVID-19 pandemic, ransomware attacks were on the rise and becoming more expensive. Now your, um, friend's organization has fallen victim and is going to pay. Here's how they should handle it.
Even prior to the COVID-19 pandemic, ransomware attacks were on the rise and becoming more expensive. Now your, um, friend's organization has fallen victim and is going to pay. Here's how they should handle it.
26 May 2020
How to Pay a Ransom
 Even prior to the COVID-19 pandemic, ransomware attacks were on the rise and becoming more expensive. Now your organization has fallen victim and is going to pay. Here's how to handle it.
Even prior to the COVID-19 pandemic, ransomware attacks were on the rise and becoming more expensive. Now your organization has fallen victim and is going to pay. Here's how to handle it.
26 May 2020
Crooks threaten to leak customer data stolen from e‑commerce sites
A hack-and-extort campaign takes aim at poorly secured databases replete with customer information that can be exploited for further attacks
The post Crooks threaten to leak customer data stolen from e‑commerce sites appeared first on WeLiveSecurity
26 May 2020
Benefits of a Cloud-Based, Automated Cyber Range
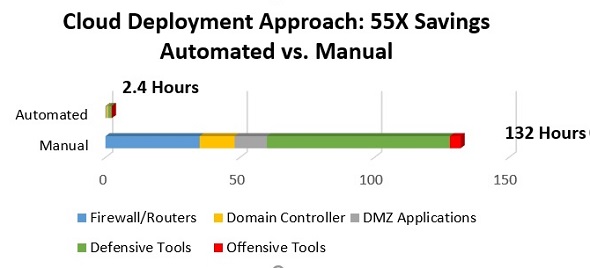 A cyber range is an irreplaceable tool that allows cybersecurity professionals to improve their response capabilities as well as their ability to identify risks.
A cyber range is an irreplaceable tool that allows cybersecurity professionals to improve their response capabilities as well as their ability to identify risks.
26 May 2020
