Cybersecurity News
Surge in Consumer-Grade IoT Devices Undermining Enterprise Security
Individuals and business groups are connecting everything from Amazon Echo devices to data-sampling sensors on networks with sensitive systems with little regard to safety, two reports show.22 July 2020
VC Investment in Cybersecurity Dips & Shifts with COVID-19
While the pandemic has infected funding for cybersecurity startups, it also has emboldened some startups with innovative tools that secure the wave of at-home work.22 July 2020
OilRig APT Drills into Malware Innovation with Unique Backdoor
 The RDAT tool uses email as a C2 channel, with attachments that hide data and commands inside images.
The RDAT tool uses email as a C2 channel, with attachments that hide data and commands inside images.
22 July 2020
Apple Security Research Device Program Draws Mixed Reactions
 Apple's Security Research Device program is now open to select researchers - but some are irked by the program's vulnerability disclosure restrictions.
Apple's Security Research Device program is now open to select researchers - but some are irked by the program's vulnerability disclosure restrictions.
22 July 2020
Twitter Hacking for Profit and the LoLs
The New York Times last week ran an interview with several young men who claimed to have had direct contact with those involved in last week's epic hack against Twitter. These individuals said they were only customers of the person who had access to Twitter's internal employee tools, and were not responsible for the actual intrusion or bitcoin scams that took place that day. But new information suggests that at least two of them operated a service that resold access to Twitter employees for the purposes of modifying or seizing control of prized Twitter profiles.22 July 2020
CISA Hires Security Experts to Boost COVID-19 Response
The agency brings in expertise from the private sector to improve its technical capabilities and engagement with industry partners.22 July 2020
North Korea's Lazarus Group Developing Cross-Platform Malware Framework
The APT group, known for its attack on Sony Pictures in 2014, has created an "advanced malware framework" that can launch and manage attacks against systems running Windows, MacOS, and Linux.22 July 2020
Ripple20's Effects Will Impact IoT Cybersecurity for Years to Come
A series of newly discovered TCP/IP software vulnerabilities pose a threat to millions of IoT devices. Undiscovered since the early 1990s, they highlight the need to improve security in an increasingly precarious IoT supply chain.22 July 2020
COVID-19-Related Attacks Exploded in the First Half of 2020
COVID-19 as part of a cyberattack increased by more than 3,900% between February and June.22 July 2020
The InfoSec Barrier to AI
Information security challenges are proving to be a huge barrier for the artificial intelligence ecosystem. Conversely, AI is causing headaches for CISOs. Here's why.22 July 2020
Lazarus Group Surfaces with Advanced Malware Framework
 The North Korean APT has been using the framework, called MATA, for a number of purposes, from spying to financial gain.
The North Korean APT has been using the framework, called MATA, for a number of purposes, from spying to financial gain.
22 July 2020
Going Down the Spyware Rabbit Hole with SilkBean Mobile Malware
 An Android spyware attack was recently discovered that targeted the Uyghur ethnic minority group - since 2013.
An Android spyware attack was recently discovered that targeted the Uyghur ethnic minority group - since 2013.
22 July 2020
Privacy watchdogs urge videoconferencing services to boost privacy protections
The open letter highlights five security and privacy principles that require heightened attention from videoconferencing services
The post Privacy watchdogs urge videoconferencing services to boost privacy protections appeared first on WeLiveSecurity
22 July 2020
Prometei botnet exploits Windows SMB to mine for cryptocurrency
The new botnet has been quietly operating since March.22 July 2020
Q&A: How Systemic Racism Weakens Cybersecurity
 Cybersecurity policy expert and attorney Camille Stewart explains how to dismantle systemic racism in the industry - and build a more diverse and representative workforce.
Cybersecurity policy expert and attorney Camille Stewart explains how to dismantle systemic racism in the industry - and build a more diverse and representative workforce.
22 July 2020
Cybersecurity Lessons from the Pandemic
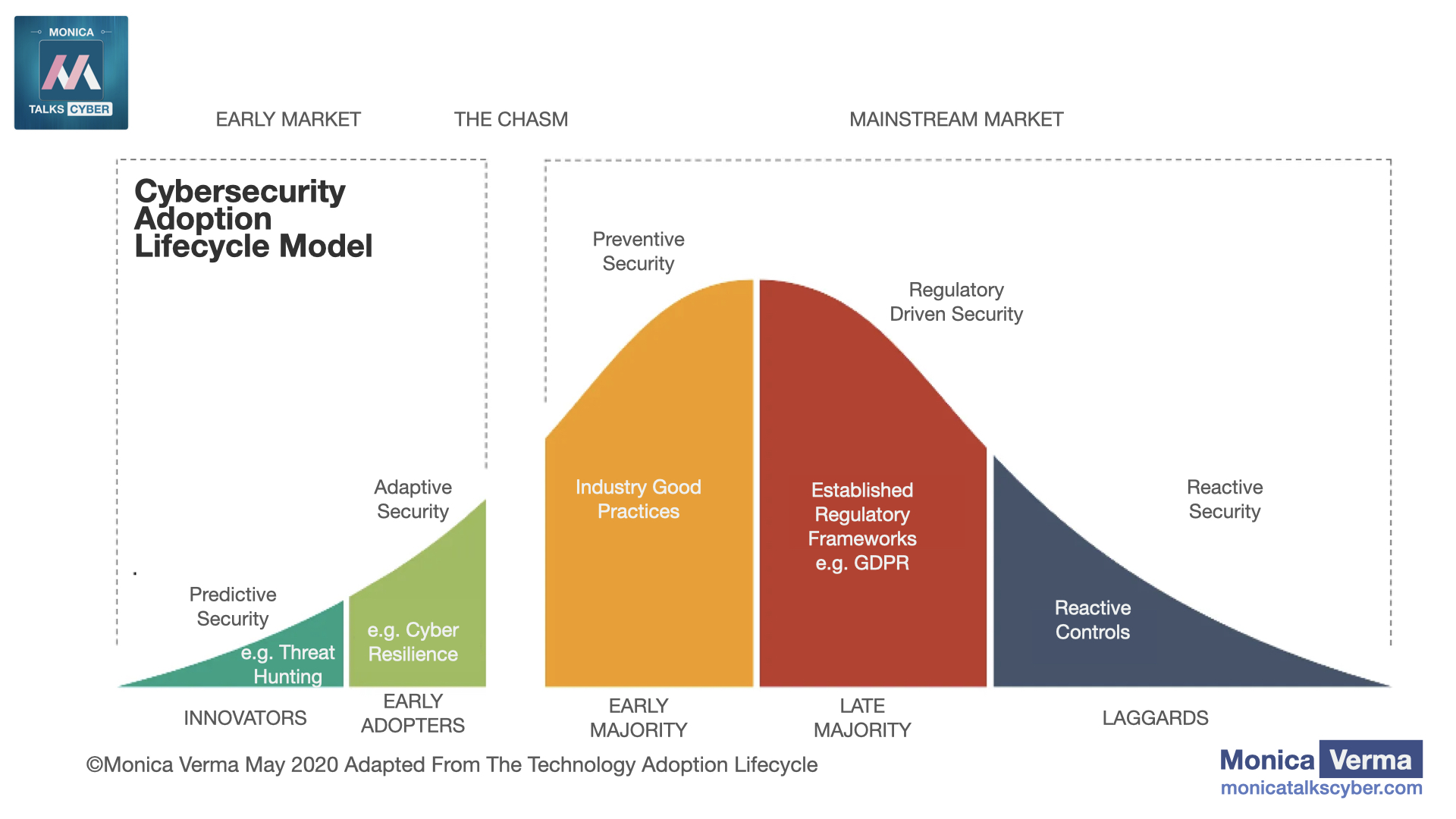 How does cybersecurity support business and society? The pandemic shows us.
How does cybersecurity support business and society? The pandemic shows us.
22 July 2020
University of York discloses data breach, staff and student records stolen
Third-party cloud service provider Blackbaud has been blamed.22 July 2020
Leak Exposes Private Data of Genealogy Service Users
 An exposed ElasticSearch server belonging to Software MacKiev put 60,000 users of Ancestry.com’s Family Tree Maker software at risk.
An exposed ElasticSearch server belonging to Software MacKiev put 60,000 users of Ancestry.com’s Family Tree Maker software at risk.
22 July 2020
Fundamentals of Network Traffic Decryption and Risk Management
Visibility into and inspection of inbound encrypted network traffic is essential for sound enterprise network security. Decryption approaches must soon change due to increasing cost and complexity, but alternative technologies are emerging.22 July 2020
Adobe issues emergency fixes for critical vulnerabilities in Photoshop, Bridge, Prelude
13 vulnerabilities, the majority critical, are being tackled in the out-of-band security update.22 July 2020
