Cybersecurity News
Look Beyond the 'Big 5' in Cyberattacks
Don't ignore cyber operations outside US and European interests, researcher says. We can learn a lot from methods used by attackers that aren't among the usual suspects.25 November 2020
Three members of TMT cybercrime group arrested in Nigeria
The TMT group has infected more than 50,000 organizations around the world with malware.25 November 2020
Major BEC Phishing Ring Cracked Open with 3 Arrests
 Some 50,000 targeted victims have been identified so far in a massive, global scam enterprise that involves 26 different malwares.
Some 50,000 targeted victims have been identified so far in a massive, global scam enterprise that involves 26 different malwares.
25 November 2020
Critical MobileIron RCE Flaw Under Active Attack
 Attackers are targeting the critical remote code-execution flaw to compromise systems in the healthcare, local government, logistics and legal sectors, among others.
Attackers are targeting the critical remote code-execution flaw to compromise systems in the healthcare, local government, logistics and legal sectors, among others.
25 November 2020
How to Update Your Remote Access Policy – And Why You Should Now
 Reducing the risks of remote work starts with updating the access policies of yesterday.
Reducing the risks of remote work starts with updating the access policies of yesterday.
25 November 2020
Prevention Is Better Than the Cure When Securing Cloud-Native Deployments
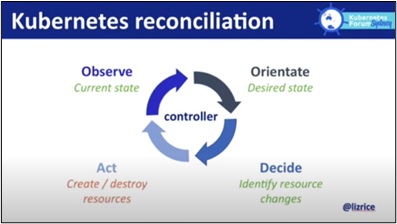 The "OODA loop" shows us how to secure cloud-native deployments and prevent breaches before they occur.
The "OODA loop" shows us how to secure cloud-native deployments and prevent breaches before they occur.
25 November 2020
Why Security Awareness Training Should Be Backed by Security by Design
Cybersecurity training needs an overhaul, though the training itself is only one small part of how security teams can influence user behavior.25 November 2020
Light-Based Attacks Expand in the Digital Home
 The team that hacked Amazon Echo and other smart speakers using a laser pointer continue to investigate why MEMS microphones respond to sound.
The team that hacked Amazon Echo and other smart speakers using a laser pointer continue to investigate why MEMS microphones respond to sound.
25 November 2020
YouTube suspends OANN for allegedly peddling fake COVID-19 cures
If the outlet wants to monetize videos in the future, it must reapply to YouTube’s member program.25 November 2020
Home Depot agrees to $17.5 million settlement over 2014 data breach
The US retailer’s point-of-sale systems were infected with malware.25 November 2020
Latest Version of TrickBot Employs Clever New Obfuscation Trick
The malware takes advantage of how the Windows command line interpreter works to try and slip past anti-detection tools, Huntress Labs says.24 November 2020
Baidu Apps Leaked Location Data, Machine Learning Reveals
Several apps available on the Google Play Store, including two made by Chinese Internet giant Baidu, leaked information about the phone's hardware and location without the user's knowledge, research finds.24 November 2020
How Ransomware Defense is Evolving With Ransomware Attacks
 As data exfiltration threats and bigger ransom requests become the norm, security professionals are advancing from the basic "keep good backups" advice.
As data exfiltration threats and bigger ransom requests become the norm, security professionals are advancing from the basic "keep good backups" advice.
24 November 2020
CISA Warns of Holiday Online Shopping Scams
The agency urges shoppers to be cautious of fraudulent websites, unsolicited emails, and unencrypted financial transactions.24 November 2020
Post-Breach, Peatix Data Reportedly Found on Instagram, Telegram
 Events application Peatix this week disclosed a data breach, after user account information reportedly began circulating on Instagram and Telegram.
Events application Peatix this week disclosed a data breach, after user account information reportedly began circulating on Instagram and Telegram.
24 November 2020
Alexa, Disarm the Victim's Home Security System
Researchers who last year hacked popular voice assistants with laser pointers take their work to the next level.24 November 2020
2FA bypass discovered in web hosting software cPanel
More than 70 million sites are managed via cPanel software, according to the company.24 November 2020
‘Minecraft Mods’ Attack More Than 1 Million Android Devices
 Fake Minecraft Modpacks on Google Play deliver millions of abusive ads and make normal phone use impossible.
Fake Minecraft Modpacks on Google Play deliver millions of abusive ads and make normal phone use impossible.
24 November 2020
Cloud Security Startup Lightspin Emerges From Stealth
The startup, founded by former white-hat hackers, has secured a $4 million seed round to close security gaps in cloud environments.24 November 2020
US Treasury's OFAC Ransomware Advisory: Navigating the Gray Areas
 Leveraging the right response strategy, following the regulations, and understanding the ransom entity are the fundamentals in any ransomware outbreak.
Leveraging the right response strategy, following the regulations, and understanding the ransom entity are the fundamentals in any ransomware outbreak.
24 November 2020
