Cybersecurity News
Hidden Dangers of Microsoft 365's Power Automate and eDiscovery Tools
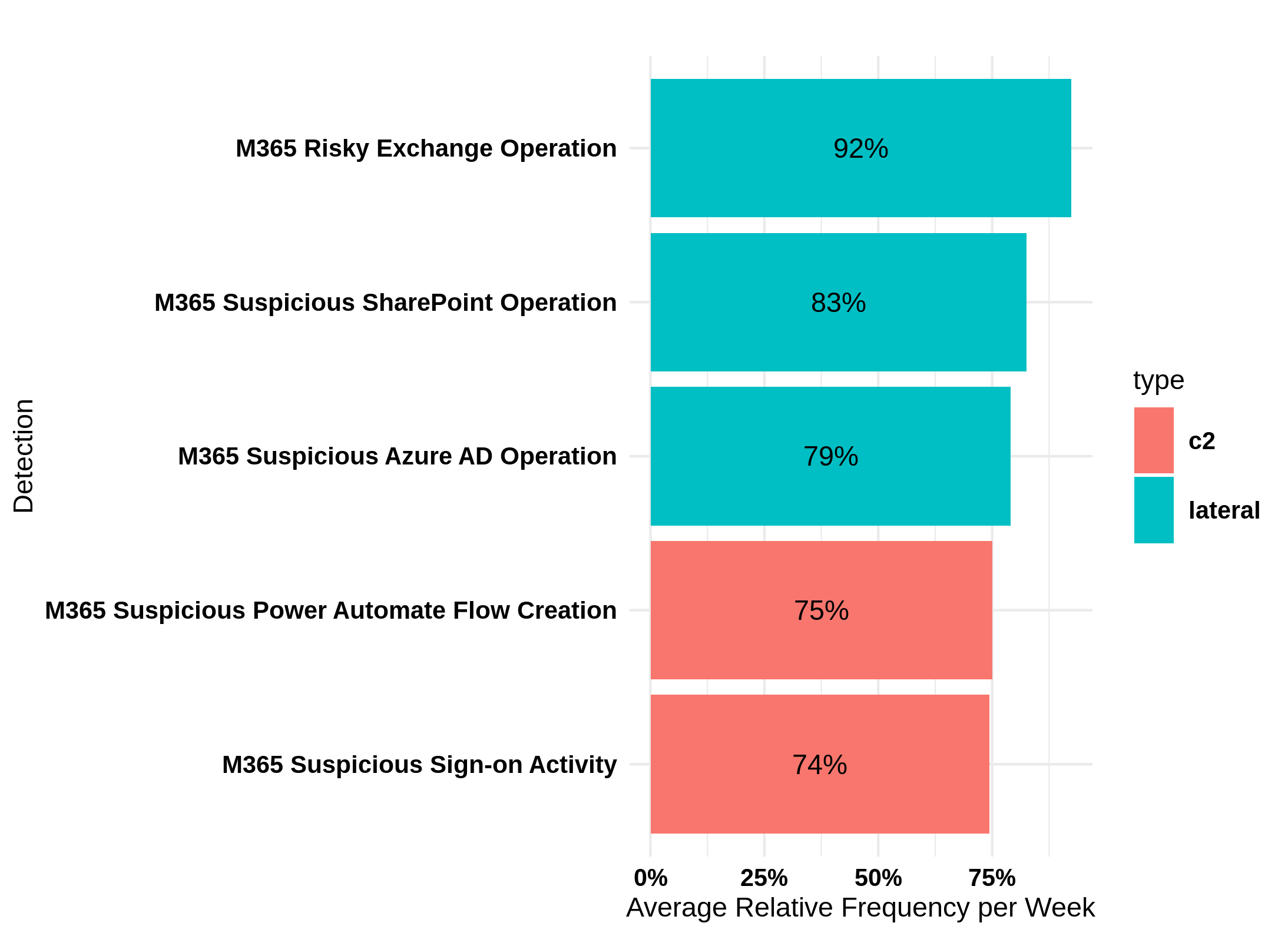 Attackers are using legitimate enterprise tools to execute attacks and carry out malicious actions. Security teams must take action now.
Attackers are using legitimate enterprise tools to execute attacks and carry out malicious actions. Security teams must take action now.
08 February 2021
Cartoon Caption Winner: Insider Threat
 And the winner of Dark Reading's January cartoon caption contest is ...
And the winner of Dark Reading's January cartoon caption contest is ...
08 February 2021
With one update, this malicious Android app hijacked millions of devices
All it takes is one tweak to change a legitimate app into a frustrating parasite on your handset.08 February 2021
Domestic Kitten hacking group strikes local citizens considered a threat to Iranian regime
FurBall spyware pretends to be everything from a security app to screen wallpapers.08 February 2021
ESET Threat Report Q4 2020
A view of the Q4 2020 threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and research experts
The post ESET Threat Report Q4 2020 appeared first on WeLiveSecurity
08 February 2021
Hacktivists deface multiple Sri Lankan domains, including Google.lk
Authorities said they detected the attack a few hours after it started and blocked it on Saturday.07 February 2021
Industrial Networks See Sharp Uptick in Hackable Security Holes
 Claroty reports that adversaries, CISOs and researchers have all turned their attention to finding critical security bugs in ICS networks.
Claroty reports that adversaries, CISOs and researchers have all turned their attention to finding critical security bugs in ICS networks.
05 February 2021
Unpatched WordPress Plugin Code-Injection Bug Afflicts 50K Sites
 An CRSF-to-stored-XSS security bug plagues 50,000 'Contact Form 7' Style users.
An CRSF-to-stored-XSS security bug plagues 50,000 'Contact Form 7' Style users.
05 February 2021
Spotify Hit With Another Credential-Stuffing Attack
This marks the second credential-stuffing attack to hit the streaming platform in the last few months.05 February 2021
Webdev tutorials site SitePoint discloses data breach
SitePoint admits data breach after one million user creds were sold on a hacking forum last December.05 February 2021
Security Researchers Push for 'Bug Bounty Program of Last Resort'
An international program that pays out hefty sums for the discovery of software vulnerabilities could spur greater scrutiny of applications and lead to better security.05 February 2021
Pro Tip: Don't Doubt Yourself
 The Edge asked seasoned security pros what they wish they had known when they first got into the field.
The Edge asked seasoned security pros what they wish they had known when they first got into the field.
05 February 2021
Week in security with Tony Anscombe
ESET unearths a supply-chain attack against an Android emulator for PC and Mac – ESET research into malware targeting HPC clusters – How to prevent at least some zero-days
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
05 February 2021
Google Chrome Zero-Day Afflicts Windows, Mac Users
 Google warns of a zero-day vulnerability in the V8 open-source engine that's being actively exploited by attackers.
Google warns of a zero-day vulnerability in the V8 open-source engine that's being actively exploited by attackers.
05 February 2021
Google Chrome sync feature can be abused for C&C and data exfiltration
A security researcher has found a malicious Chrome extension in the wild abusing the Chrome Sync process.05 February 2021
Ransomware Attacks Hit Major Utilities
 Electrobras, the largest power company in Latin America, faced a temporary suspension of some operations.
Electrobras, the largest power company in Latin America, faced a temporary suspension of some operations.
05 February 2021
Cybercrime Goes Mainstream
Organized cybercrime is global in scale and the second-greatest risk over the next decade.05 February 2021
AI and APIs: The A+ Answers to Keeping Data Secure and Private
 Many security leaders view regulations and internal processes designed to manage and secure data as red tape that hampers innovation. Nothing could be further from the truth.
Many security leaders view regulations and internal processes designed to manage and secure data as red tape that hampers innovation. Nothing could be further from the truth.
05 February 2021
Woman pleads guilty for using gov’t PC to steal photos of 'snitches' in Iowa
The photos were shared in a group dedicated to outing “law enforcement cooperators.”05 February 2021
Founder of cryptocurrency hedge funds charged over $90 million theft
Clients were allegedly lied to when they queried where their funds were being invested.05 February 2021
