Cybersecurity News
WhatsApp will limit features for users who don’t accept new data‑sharing rules
Your account won’t be deleted, but here's what you may want to be aware of if not even repeated reminders do the trick
The post WhatsApp will limit features for users who don’t accept new data‑sharing rules appeared first on WeLiveSecurity
11 May 2021
Colonial Pipeline ransomware attack: Everything you need to know
Updated: DarkSide has claimed responsibility for the catastrophic ransomware outbreak.11 May 2021
Everything you need to know about the Colonial Pipeline ransomware attack
DarkSide has claimed responsibility for the catastrophic ransomware outbreak.11 May 2021
GitHub shifts away from passwords with security key support for SSH Git operations
Support has been added to bolster defense against account compromise.11 May 2021
Virtual Private Networks
Virtual Private Networks (VPN) create encrypted tunnels when you connect to the Internet. They are a fantastic way to protect your privacy and data, especially when traveling and connecting to untrusted or unknown networks, such as at hotels or coffee shops. Use a VPN whenever possible, both for work and personal use.11 May 2021
Colonial Pipeline Cyberattack: What Security Pros Need to Know
As the massive US pipeline operator works to restore operations after a DarkSide ransomware attack late last week, experts say it's a cautionary tale for critical infrastructure providers.10 May 2021
Tulsa Deals with Aftermath of Ransomware Attack
Weekend attack shuts down several city sites and service.10 May 2021
Four Plead Guilty to RICO Conspiracy Involving Hosting Services for Cybercrime
The "bulletproof hosting" organization hosted malware including Zeus, SpyEye, Citadel, and the Blackhole Exploit Kit.10 May 2021
DarkSide explained: the ransomware group responsible for Colonial Pipeline cyberattack
The group's existence is tied to a murky web of shorted stocks, criminality, and failed attempts to appear as Robin Hood.10 May 2021
Colonial Pipeline’s Ransomware Attack Sparks Emergency Declaration
 Security researchers mull possible perpetrators of the attack, and warned that the incident could be a harbinger of things to come.
Security researchers mull possible perpetrators of the attack, and warned that the incident could be a harbinger of things to come.
10 May 2021
Lemon Duck Cryptojacking Botnet Changes Up Tactics
 The sophisticated threat is targeting Microsoft Exchange servers via ProxyLogon in a wave of fresh attacks against North American targets.
The sophisticated threat is targeting Microsoft Exchange servers via ProxyLogon in a wave of fresh attacks against North American targets.
10 May 2021
10 Security Awareness Training Mistakes to Avoid
 Give your cybersecurity culture a boost by adding these to the "don't" column of your cybersecurity awareness training do's and don'ts list.
Give your cybersecurity culture a boost by adding these to the "don't" column of your cybersecurity awareness training do's and don'ts list.
10 May 2021
Fintech Startup Offers $500 for Payroll Passwords
How much is your payroll data worth? Probably a lot more than you think. One financial startup that's targeting the gig worker market is offering up to $500 to anyone willing to hand over the payroll account username and password given to them by their employer, plus a regular payment for each month afterwards in which those credentials still work.10 May 2021
Exchange Exploitation: Not Dead Yet
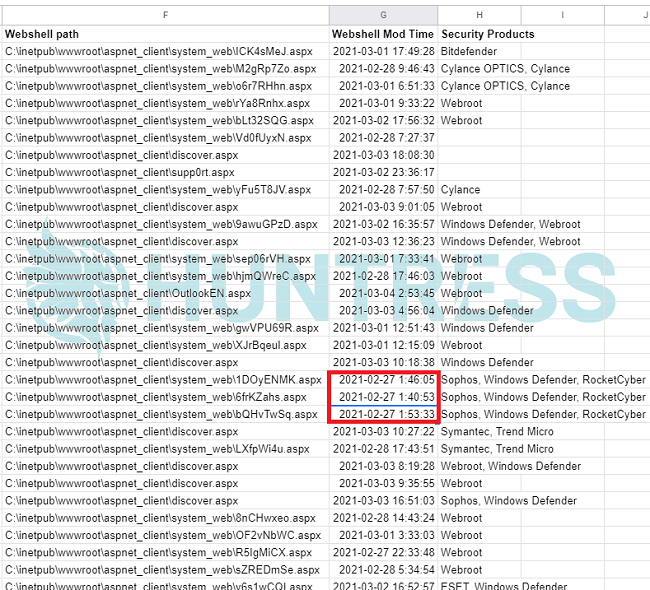 The mass exploitation of Exchange Servers has been a wake-up call, and it will take all parties playing in concert for the industry to react, respond, and recover.
The mass exploitation of Exchange Servers has been a wake-up call, and it will take all parties playing in concert for the industry to react, respond, and recover.
10 May 2021
Amazon seized, destroyed two million fake products sent to warehouses in 2020
Over 10 billion suspect listings were also wiped out during the year in a counterfeit crackdown.10 May 2021
Lemon Duck hacking group adopts Microsoft Exchange Server vulnerabilities in new attacks
Fake TLDs are now also being created to maximize the potential success of attacks.10 May 2021
Group pleads guilty to running bulletproof hosting service for criminal gangs, malware payloads
Zeus, SpyEye, Citadel, and the Blackhole exploit kit were among the strains stored through the host.10 May 2021
Major U.S. Pipeline Crippled in Ransomware Attack
 Colonial Pipeline Company says it is the victim of a cyberattack that forced the major provider of liquid fuels to the East Coast to temporarily halted all pipeline operations.
Colonial Pipeline Company says it is the victim of a cyberattack that forced the major provider of liquid fuels to the East Coast to temporarily halted all pipeline operations.
08 May 2021
iPhone Hack Allegedly Used to Spy on China’s Uyghurs
 U.S. intelligence said that the Chaos iPhone remote takeover exploit was used against the minority ethnic group before Apple could patch the problem.
U.S. intelligence said that the Chaos iPhone remote takeover exploit was used against the minority ethnic group before Apple could patch the problem.
07 May 2021
How North Korean APT Kimsuky Is Evolving Its Tactics
Researchers find differences in Kimsuky's operations that lead them to divide the APT into two groups: CloudDragon and KimDragon.07 May 2021
