Cybersecurity News
Android stalkerware threatens victims further and exposes snoopers themselves
ESET research reveals that common Android stalkerware apps are riddled with vulnerabilities that further jeopardize victims and expose the privacy and security of the snoopers themselves
The post Android stalkerware threatens victims further and exposes snoopers themselves appeared first on WeLiveSecurity
How Apple’s AirTag turns us into unwitting spies in a vast surveillance network

The tech giant says it has security safeguards in place. But these tracking devices can be hacked and put to other nefarious purposes
Apple has launched the latest version of its operating system, iOS 14.5, which features the much-anticipated app tracking transparency function, bolstering the tech giant’s privacy credentials.
But iOS 14.5 also introduced support for the new Apple AirTag, which risks doing the opposite.
Related: Apple launches new iMac, iPad Pro, AirTags and Podcast subscriptions
Being around someone with an AirTag is *very* annoying pic.twitter.com/GZj8ZeTCck
A security researcher has found out the microcontroller inside Apple's #AirTag can be reprogrammed, opening the door to AirTag modifications and potential malicious uses. https://t.co/PAKPZab7Ov pic.twitter.com/UVTvPl41Sn
Amazon Sidewalk could help extend the reach of your Wi-Fi, but the company's data-collection habits may outweigh the feature's benefits. https://t.co/gcCKqLJDFy
Continue reading...Rapid7 Source Code Accessed in Supply Chain Attack
An investigation of the Codecov attack revealed intruders accessed Rapid7 source code repositories containing internal credentials and alert-related data.Verizon’s 2021 DBIR: Phishing and ransomware threats looming ever larger
The report provides unique insights into how the COVID-19 pandemic affected the data breach landscape
The post Verizon’s 2021 DBIR: Phishing and ransomware threats looming ever larger appeared first on WeLiveSecurity
FIN7 Backdoor Masquerades as Ethical Hacking Tool
 The financially motivated cybercrime gang behind the Carbanak RAT is back with the Lizar malware, which can harvest all kinds of info from Windows machines.
The financially motivated cybercrime gang behind the Carbanak RAT is back with the Lizar malware, which can harvest all kinds of info from Windows machines.
How Faster COVID-19 Research Is Being Made Possible by Secure Silicon
 When Intel and Leidos set up a "trusted execution environment" to enable a widespread group of researchers to securely share and confidentially compute real-world data, it was no small achievement.
When Intel and Leidos set up a "trusted execution environment" to enable a widespread group of researchers to securely share and confidentially compute real-world data, it was no small achievement.
Cisco Confirms Plans to Acquire Kenna Security
Cisco plans to integrate Kenna's vulnerability management technology into its SecureX platform.DarkSide Ransomware Suffers ‘Oh, Crap!’ Server Shutdowns
 The RaaS that crippled Colonial Pipeline lost the servers it uses to pull off ransomware attacks, while REvil’s gonads shrank in response.
The RaaS that crippled Colonial Pipeline lost the servers it uses to pull off ransomware attacks, while REvil’s gonads shrank in response.
Week in security with Tony Anscombe
Join ESET Research at RSA Conference 2021 – WhatsApp to restrict features for some users – 1 million apps rejected from the App Store last year
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
DarkSide Ransomware Gang Quits After Servers, Bitcoin Stash Seized
The DarkSide ransomware affiliate program responsible for the six-day outage at Colonial Pipeline this week that led to fuel shortages and price spikes across the country is running for the hills. The crime gang announced it was closing up shop after its servers were seized and someone drained funds from an account the group uses to pay affiliates.Chart: Cybersecurity Now a Top Corporate Priority
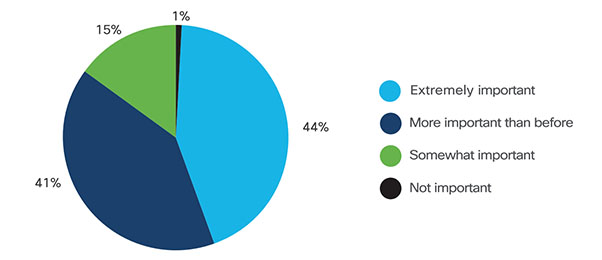 Majority of global IT decision makers say cybersecurity is extremely or more important now than it was pre-pandemic, according to Cisco.
Majority of global IT decision makers say cybersecurity is extremely or more important now than it was pre-pandemic, according to Cisco.
SOC Teams Burdened by Alert Fatigue Explore XDR
ESG research finds a complex attack surface and threat landscape make alerts too overwhelming to monitor accuratelyWi-Fi Design, Implementation Flaws Allow a Range of Frag Attacks
Every Wi-Fi product is affected by at least one fragmentation and aggregation vulnerability, which could lead to a machine-in-the-middle attack, researcher says.‘Scheme Flooding’ Allows Websites to Track Users Across Browsers
 A flaw that allows browsers to enumerate applications on a machine threatens cross-browser anonymity in Chrome, Firefox, Microsoft Edge, Safari and even Tor.
A flaw that allows browsers to enumerate applications on a machine threatens cross-browser anonymity in Chrome, Firefox, Microsoft Edge, Safari and even Tor.
Security Trends to Follow at RSA Conference 2021
Here are three key categories of sessions that provide an inside look at some of today's most interesting cybersecurity trends.Verizon: Pandemic Ushers in ⅓ More Cyber-Misery
 The DBRI – Verizon’s 2021 data breach report – shows spikes in sophisticated phishing, financially motivated cyberattacks and a criminal focus on web-application servers.
The DBRI – Verizon’s 2021 data breach report – shows spikes in sophisticated phishing, financially motivated cyberattacks and a criminal focus on web-application servers.
Ransomware’s New Swindle: Triple Extortion
 Ransomware attackers are now demanding cash from the customers of victims too.
Ransomware attackers are now demanding cash from the customers of victims too.
How to Get into the Bug-Bounty Biz: The Good, Bad and Ugly
 Experts from Intel, GitHub and KnowBe4 weigh in on what you need to succeed at security bug-hunting.
Experts from Intel, GitHub and KnowBe4 weigh in on what you need to succeed at security bug-hunting.
