Cybersecurity News
Expecting the Unexpected: Tips for Effectively Mitigating Ransomware Attacks in 2021
Cybercriminals continually innovate to thwart security protocols, but organizations can take steps to prevent and mitigate ransomware attacks.23 June 2021
ChaChi: a new GoLang Trojan used in attacks against US schools
The malware has found a role to play in ransomware strikes.23 June 2021
How Cyber Sleuths Cracked an ATM Shimmer Gang
In 2015, police departments worldwide started finding ATMs compromised with advanced new "shimming" devices made to clone data from chip card transactions. Authorities in the United States and abroad had seized many of these shimmers, but for years couldn't decrypt the data on the devices. This is a story of ingenuity and happenstance, and how one former Secret Service agent helped crack a code that revealed the contours of a global organized crime ring.23 June 2021
Unpatched Linux Marketplace Bugs Allow Wormable Attacks, Drive-By RCE
 A pair of zero-days affecting Pling-based marketplaces could allow for some ugly attacks on unsuspecting Linux enthusiasts -- with no patches in sight.
A pair of zero-days affecting Pling-based marketplaces could allow for some ugly attacks on unsuspecting Linux enthusiasts -- with no patches in sight.
23 June 2021
SonicWall ‘Botches’ October Patch for Critical VPN Bug
 Company finally rolls out the complete fix this week for an RCE flaw affecting some 800,000 devices that could result in crashes or prevent users from connecting to corporate resources.
Company finally rolls out the complete fix this week for an RCE flaw affecting some 800,000 devices that could result in crashes or prevent users from connecting to corporate resources.
23 June 2021
How to tell if a website is safe
It can be difficult to tell a legitimate website apart from an unsafe one – follow these steps to identify and protect yourself from bad websites
The post How to tell if a website is safe appeared first on WeLiveSecurity
23 June 2021
Despite Heightened Cyber-Risks, Few Security Leaders Report to CEO
A new report suggests that top management at most companies still don't get security.22 June 2021
BEC Losses Top $1.8B as Tactics Evolve
 BEC attacks getting are more dangerous, and smart users are the ones who can stop it.
BEC attacks getting are more dangerous, and smart users are the ones who can stop it.
22 June 2021
Cryptominers Slither into Python Projects in Supply-Chain Campaign
 These code bombs lurk in the PyPI package repository, waiting to be inadvertently baked into software developers' applications.
These code bombs lurk in the PyPI package repository, waiting to be inadvertently baked into software developers' applications.
22 June 2021
Transmit Security Announces $543M Series A Funding Round
The passwordless technology provider says the funding will be used to increase its reach and expand primary business functions.22 June 2021
Paving the way: Inspiring Women in Payments - A Q&A featuring Sherri Collis
Sherri Collis spent most of her career as the lone female in the conference room, occupying roles more regularly filled by men. She was overlooked for training opportunities. She was passed up for promotions. But these experiences only fueled her drive to achieve success. In this edition of our blog, Sherri explains that, contrary to popular belief, women do not need to have 100% of the qualifications to do the job and still be successful.
22 June 2021
Email Bug Allows Message Snooping, Credential Theft
 A year-old proof-of-concept attack that allows an attacker to bypass TLS email protections to snoop on messages has been patched.
A year-old proof-of-concept attack that allows an attacker to bypass TLS email protections to snoop on messages has been patched.
22 June 2021
Chart: Strength in Numbers
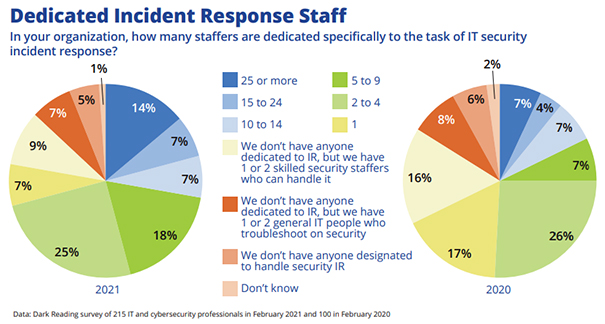 More companies are heeding expert advice to beef up their incident-response teams.
More companies are heeding expert advice to beef up their incident-response teams.
22 June 2021
NSA Funds Development & Release of D3FEND Framework
The framework, now available through MITRE, provides countermeasures to attacks.22 June 2021
Identity Eclipses Malware Detection at RSAC Startup Competition
All 10 finalists in the Innovation Sandbox were focused on identity, rather than security's mainstay for the last 20 years: Malware detection.22 June 2021
Majority of Web Apps in 11 Industries Are Vulnerable All the Time
Serious vulnerabilities exist every day in certain industries, including utilities, public administration, and professional services, according to testing data.22 June 2021
Kids’ Apps on Google Play Rife with Privacy Violations
 One in five of the most-popular apps for kids under 13 on Google Play don't comply with COPPA regulations on how children's information is collected and used.
One in five of the most-popular apps for kids under 13 on Google Play don't comply with COPPA regulations on how children's information is collected and used.
22 June 2021
Lexmark Printers Open to Arbitrary Code-Execution Zero-Day
 “No remedy available as of June 21, 2021," according to the researcher who discovered the easy-to-exploit, no-user-action-required bug.
“No remedy available as of June 21, 2021," according to the researcher who discovered the easy-to-exploit, no-user-action-required bug.
22 June 2021
7 Powerful Cybersecurity Skills the Energy Sector Needs Most
 Those looking to join the fight might want to polish up or acquire some (or all) of these hottest skills on the market.
Those looking to join the fight might want to polish up or acquire some (or all) of these hottest skills on the market.
22 June 2021
Does Your Cyberattack Plan Include a Crisis Communications Strategy? 5 Tips to Get Started
Don't overlook crisis communications in your cybersecurity incident response planning.22 June 2021

