Cybersecurity News
Actively Exploited Windows Zero-Day Gets a Patch
 Microsoft's August 2021 Patch Tuesday addressed a smaller set of bugs than usual, including more Print Spooler problems, a zero-day and seven critical vulnerabilities.
Microsoft's August 2021 Patch Tuesday addressed a smaller set of bugs than usual, including more Print Spooler problems, a zero-day and seven critical vulnerabilities.
Microsoft Patch Tuesday, August 2021 Edition
Microsoft today released software updates to plug at least 44 security vulnerabilities in its Windows operating systems and related products. The software giant warned that attackers already are pouncing on one of the flaws, which ironically enough involves an easy-to-exploit bug in the software component responsible for patching Windows 10 PCs and Windows Server 2019 machines.Microsoft's August 2021 Patch Tuesday: 44 flaws fixed, seven critical including Print Spooler vulnerability
The latest Patch Tuesday sees Microsoft release fixes for 44 different vulnerabilities, including the much-discussed Print Spooler flaw.eCh0raix Ransomware Variant Targets QNAP, Synology NAS Devices
 Some bad actors are honing tools to go after small fry: This variant was refined to target not one, but two vendors’ devices that are common in SOHO setups.
Some bad actors are honing tools to go after small fry: This variant was refined to target not one, but two vendors’ devices that are common in SOHO setups.
Deepfakes – the bot made me do it
As fraud involving highly believable synthetic media soars, what can you do to avoid getting scammed?
The post Deepfakes – the bot made me do it appeared first on WeLiveSecurity
Back-to-Basics: Use Strong Encryption
As small and medium businesses begin to re-open following the pandemic, it’s important to do so securely in order to protect customer’s payment card data. Too often, data breaches happen as a result of vulnerabilities that are entirely preventable. The PCI Security Standards Council (PCI SSC) has developed a set of payment protection resources for small businesses. In this 8-part back-to-basics series, we highlight payment security basics for protecting against payment data theft. Today’s blog focuses on using encryption to make payment data unreadable.
Chaos Malware Walks Line Between Ransomware and Wiper
 The dangerous malware has been rapidly developed since June and could be released into the wild soon.
The dangerous malware has been rapidly developed since June and could be released into the wild soon.
Fuzz Off: How to Shake Up Code to Get It Right – Podcast
 Is fuzzing for the cybersec elite, or should it be accessible to all software developers? FuzzCon panelists say join the party as they share fuzzing wins & fails.
Is fuzzing for the cybersec elite, or should it be accessible to all software developers? FuzzCon panelists say join the party as they share fuzzing wins & fails.
1M Stolen Credit Cards Hit Dark Web for Free
 A dump of hundreds of thousands of active accounts is aimed at promoting AllWorld.Cards, a recently launched cybercriminal site for selling payment credentials online.
A dump of hundreds of thousands of active accounts is aimed at promoting AllWorld.Cards, a recently launched cybercriminal site for selling payment credentials online.
Ransomware runs rampant, so how can you combat this threat?
A new paper explains how ransomware has become one of the top cyberthreats of the day and how your organization can avoid becoming the next victim
The post Ransomware runs rampant, so how can you combat this threat? appeared first on WeLiveSecurity
‘Glowworm’ Attack Turns Power Light Flickers into Audio
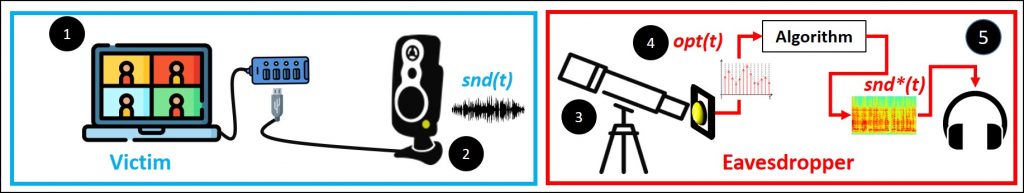 Researchers have found an entirely new attack vector for eavesdropping on Zoom and other virtual meetings.
Researchers have found an entirely new attack vector for eavesdropping on Zoom and other virtual meetings.
Black Hat: Scaling Automated Disinformation for Misery and Profit
 Researchers demonstrated the power deep neural networks enlisted to create a bot army with the firepower to shape public opinion and spark QAnon 2.0.
Researchers demonstrated the power deep neural networks enlisted to create a bot army with the firepower to shape public opinion and spark QAnon 2.0.
Auth Bypass Bug Exploited, Affecting Millions of Routers
 A mere three days after disclosure, cyberattackers are hijacking home routers from 20 vendors & ISPs to add them to a Mirai-variant botnet used for carrying out DDoS attacks.
A mere three days after disclosure, cyberattackers are hijacking home routers from 20 vendors & ISPs to add them to a Mirai-variant botnet used for carrying out DDoS attacks.
How to find and remove spyware from your phone
Surveillance isn't just the purview of nation-states and government agencies -- sometimes, it's closer to home.DEF CON 29: Satellite hacking 101
How peering into the innards of a future satellite can make cybersecurity in space more palatable
The post DEF CON 29: Satellite hacking 101 appeared first on WeLiveSecurity
Android Malware ‘FlyTrap’ Hijacks Facebook Accounts
 Coupon codes for Netlifx or Google AdWords? Voting for the best football team? Beware: Malicious apps offering such come-ons could inflict a new trojan.
Coupon codes for Netlifx or Google AdWords? Voting for the best football team? Beware: Malicious apps offering such come-ons could inflict a new trojan.
Phishing Sites Targeting Scammers and Thieves
I was preparing to knock off work on a recent Friday evening when a curious and annoying email came in via the contact form on this site: “Hello I go by the username Nuclear27 on your site Briansclub[.]com,” wrote “Mitch,” confusing me with the proprietor of perhaps the underground’s largest bazaar for stolen credit and identity data. “I made a deposit to my wallet on the site but nothing has shown up yet and I would like to know why.” Several things stood out in Mitch’s message. For starters, that is not the actual domain for BriansClub. And it’s not hard to see why Mitch got snookered: The real BriansClub site is currently not at the top of search results when one queries that shop name at Google.Cutting Through the Noise from Daily Alerts
 The biggest challenge for security teams today is the quality of the threat intelligence platforms and feeds. How much of the intel is garbage and unusable? Threat intelligence process itself spans and feeds into many external and internal systems and applications. Without actionable data, it is impossible to understand the relevance and potential impact of a threat. Learn how Threat Intelligence management plays a role to help prioritize and act fast.
The biggest challenge for security teams today is the quality of the threat intelligence platforms and feeds. How much of the intel is garbage and unusable? Threat intelligence process itself spans and feeds into many external and internal systems and applications. Without actionable data, it is impossible to understand the relevance and potential impact of a threat. Learn how Threat Intelligence management plays a role to help prioritize and act fast.
IISpy: A complex server‑side backdoor with anti‑forensic features
The second in our series on IIS threats dissects a malicious IIS extension that employs nifty tricks in an attempt to secure long-term espionage on the compromised servers
The post IISpy: A complex server‑side backdoor with anti‑forensic features appeared first on WeLiveSecurity
Password of three random words better than complex variation, experts say

UK National Cyber Security Centre recommends approach for improved combination of usability and safety
It is far better to concoct passwords made up of three random words than to use more complex variations involving streams of letters, numbers and symbols, UK government experts have said.
The National Cyber Security Centre (NCSC), part of Government Communications Headquarters, highlighted its “three random words” recommendation in a new blogpost.
Continue reading...
