Fintech Giant Fiserv Used Unclaimed Domain
If you sell Web-based software for a living and ship code that references an unregistered domain name, you are asking for trouble. But when the same mistake is made by a Fortune 500 company, the results can range from costly to disastrous. Here’s the story of one such goof committed by Fiserv [NASDAQ:FISV], a $15 billion firm that provides online banking software and other technology solutions to thousands of financial institutions.

In November 2020, KrebsOnSecurity heard from security researcher Abraham Vegh, who noticed something odd while inspecting an email from his financial institution.
Vegh could see the message from his bank referenced a curious domain: defaultinstitution.com. A quick search of WHOIS registration records showed the domain was unregistered. Wondering whether he might receive email communications to that address if he registered the domain, Vegh snapped it up for a few dollars, set up a catch-all email account for it, and waited.
“It appears that the domain is provided as a default, and customer bank IT departments are either assuming they don’t need to change it, or are not aware that they could/should,” Vegh said, noting that a malicious person who stumbled on his discovery earlier could have had a powerful, trusted domain from which to launch email phishing attacks.
At first, only a few wayward emails arrived. Ironically enough, one was from a “quality assurance” manager at Fiserv. The automatic reply message stated that the employee was out of the office “on R&R” and would be back to work on Dec. 14.
Many other emails poured in, including numerous “bounced” messages delivered in reply to missives from Cashedge.com, a money transfer service that Fiserv acquired in 2011.
Emails get bounced — or returned to the sender — when they are sent to an address that doesn’t exist or that is no longer active. The messages had been sent to an email address for a former client solutions director at Fiserv; the “reply-to:” address in those missives was “donotreply@defaultinstitution.com”.
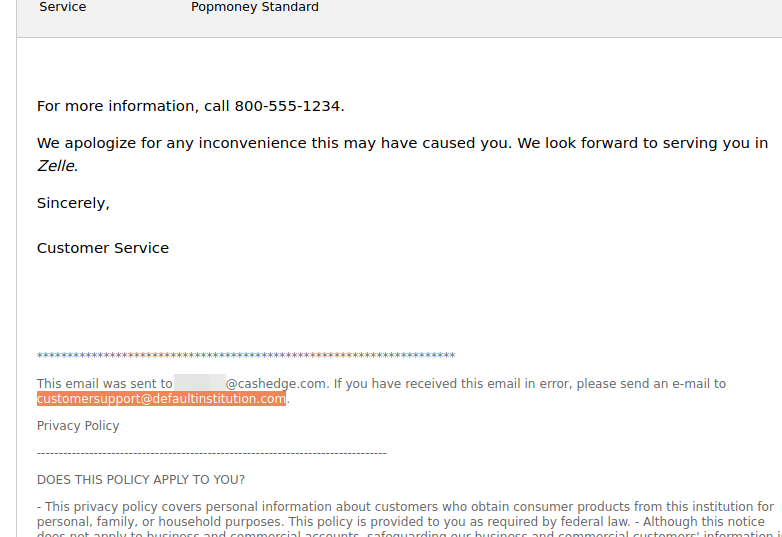
The messages were informing customers of CashEdge’s main service Popmoney — which lets users send, request and receive money directly from bank accounts — that Popmoney was being replaced with Zelle, a more modern bank-to-bank transfer service.
Each CashEdge missive included information about recurring transfers that were being canceled, such as the plan ID, send date, amount to be transferred, the name and last four digits of the account number the money was coming from, and the email address of the recipient account.
Incredibly, at the bottom of every message to CashEdge/Popmoney customers was a boilerplate text: “This email was sent to [recipient name here]. If you have received this email in error, please send an e-mail to customersupport@defaultinstitution.com.”
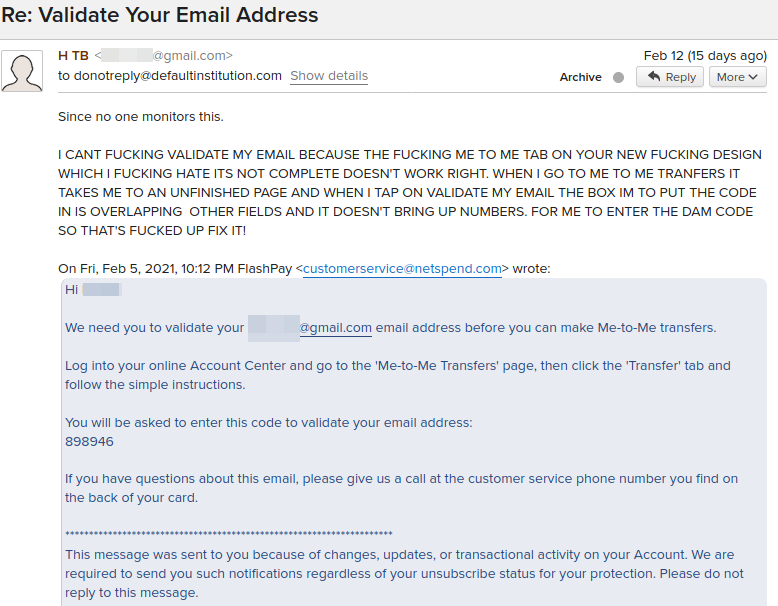
Other services that directed customers to reply to the researcher’s domain included Fiserv customer Netspend.com, a leading provider of prepaid debit cards that require no minimum balance or credit check. The messages from Netspend all were to confirm the email address tied to a new account, and concerned “me-to-me transfers” set up through its service.
Each message included a one-time code that recipients were prompted to enter at the company’s website. But from reading the many replies to these missives, it seems Netspend didn’t make it terribly obvious where users were supposed to input this code. Here’s one of the more profane examples of a customer response:
Many others emailed by Netspend expressed mystification as to why they were receiving such messages, stating they’d never signed up for the service. From the gist of those messages, the respondents were victims of identity fraud.
“My accounts were hacked and if any funding is gone your [sic] sued from me and federal trade commission,” one wrote. “I didn’t create the account. Please stop this account and let me know what’s going on,” replied another. “I never signed up for this service. Someone else is using my information,” wrote a third.
Those messages also concerned me-to-me transfers. Other emails came from Detroit-based TCF National Bank.
New York-based Union Bank also sent customer information to the researcher’s domain. Both of those messages were intended to confirm that the recipient had tied their accounts to those at another bank. And in both cases, the recipients replied that they had not authorized the linkage.
In response to questions from KrebsOnSecurity, Fiserv acknowledged that it had inadvertently included references to defaultinstitution.com as a placeholder in software solutions used by some partners.
“We have identified 5 clients for which auto-generated emails to their customers included the domain name “defaultinstitution.com” in the “reply-to” address,” Fiserv said in a written statement. “This placeholder URL was inadvertently left unchanged during implementation of these solutions. Upon being made aware of the situation we immediately conducted an analysis to locate and replace instances of the placeholder domain name. We have also notified the clients whose customers received these emails.”
Indeed, the last email Vegh’s inbox received was on Feb. 26.
This is not the first time an oversight by Fiserv has jeopardized the security and privacy of its customers. In 2018, KrebsOnSecurity revealed how a programming weakness in a software platform sold to hundreds of banks exposed personal and financial data of countless customers. Fiserv was later sued over the matter by a credit union customer; that lawsuit is still proceeding.
Vegh said he found a similar domain goof while working as a contractor at the Federal Reserve Bank of Philadelphia back in 2015. In that instance, he discovered an unregistered domain invoked by AirWatch, a mobile device management product since acquired by VMWare.
“After registering that domain I started getting traffic from all around the world from Fortune 500 company devices pinging the domain,” Vegh said.
Vegh said he plans to give Fiserv control over defaultinstitution.com, and hand over the messages intercepted by his inbox. He’s not asking for much in return.
“I had been promised a t-shirt and a case of beer for my efforts then, but alas, never received one,” he said of his interaction with AirWatch. “This time, I am hoping to actually receive a t-shirt!”
Update, 12:44 p.m. ET: The lead paragraph has been updated to reflect Fiserv’s 2020 revenues, which were nearly $15 billion.
>>More
