Nmap Online
Nmap
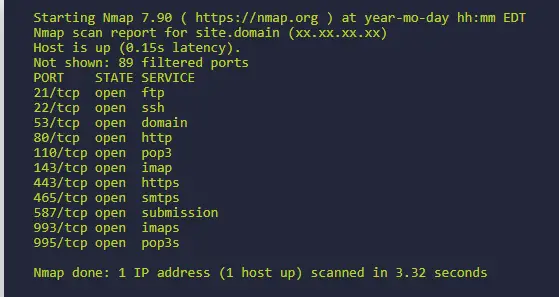
Nmap is a free and open-source network scanner. Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses.
Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection. These features are extensible by scripts that provide more advanced service detection, vulnerability detection, and other features. Nmap can adapt to network conditions including latency and congestion during a scan.
Recent scans
| Domain or IP | Scan type | Size |
|---|---|---|
| 91.228.54.54 | Fast Scan | 303 |
| ukb.ed.ao | Fast Scan | 205 |
| api.mensaoffice.de | Fast Scan | 345 |
| sportshop.winterthur.ch | OS Detection | 1145 |
| 164.132.171.111 | Fast Scan | 325 |
| 85.159.24.137 | Fast Scan | 277 |
| 212.163.31.59 | Fast Scan | 205 |
| 217.117.132.100 | Fast Scan | 205 |
| 71.19.146.161 | Fast Scan | 357 |
| 85.142.160.226 | Fast Scan | 278 |
Nmap Online By the numbers
23,000+
cybersecurity experts
1,000,000+
scanned hosts
online nmap
#1 google search result by keyword
Cybersecurity News
Latest news from Cyber Security industry
International sting takes down online marketplace of stolen identities
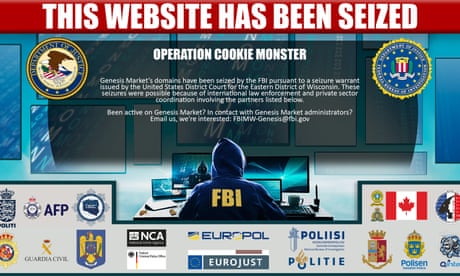
Operation led by FBI and Dutch police with involvement of UK National Crime Agency takes Genesis Market offline
A criminal online marketplace selling millions of stolen identities for as little as 56p has been taken down in an international crackdown.
The sting, led by the FBI and Dutch police with the involvement of law enforcement agencies across 18 countries, including the UK’s National Crime Agency (NCA), took Genesis Market offline on Tuesday evening.
Continue reading...Why you should spring clean your home network and audit your backups
Do you know how many devices are connected to your home network? You don’t? This is precisely why it’s time for a network audit.
The post Why you should spring clean your home network and audit your backups appeared first on WeLiveSecurity